
Telegram zero-day vulnerability bounties are exploding, and none more shocking than this:
“We’re offering up to $4,000,000 for a full-chain, zero-click Telegram exploit.”
This isn’t fiction. It’s a real bounty issued by Operation Zero, a Russian exploit broker. Telegram is now the most lucrative target in the global zero-day market. This was not a rumor, leak, or underground forum post. It was a formal, tiered bounty posted by Operation Zero, a well-known exploit dealer that pays top dollar for exclusive cyberweapons. The payout was not just massive; it was a clear signal to intelligence agencies, cybersecurity professionals, and authoritarian regimes alike: Telegram is now a high-value target in global cyberwarfare.
Telegram boasts over 900 million monthly active users across the globe. Its adoption spans from everyday consumers to journalists, activists, politicians, and military personnel. Yet despite its reputation for privacy, Telegram’s infrastructure includes a Telegram security flaw. Most chats are not end-to-end encrypted by default, and its cloud-based architecture means messages are routinely stored and processed on Telegram’s centralized servers.
A Telegram zero-day vulnerability has the potential to go far beyond standard bugs or glitches. These Telegram zero-day vulnerability issues can allow remote access to messages, hijacking of accounts, and full-device compromise, even without any interaction from the user. In such cases, hostile actors could impersonate individuals, steal sensitive data, or track communications in real time. For governments seeking mass surveillance or cyber suppression, Telegram, with its Telegram privacy concerns, is increasingly viewed as a gateway into personal and political ecosystems.
This article breaks down how the zero-day exploit market works, why Telegram has become a central focus of state-aligned bounty programs, and what users can do to reduce their risk. We will also explore Telegram’s flawed encryption model, its history of security lapses, and the broader implications for encrypted messaging apps worldwide. If you want weekly insights like this at the intersection of AI, cyberwarfare, and digital privacy, subscribe to the Quantum Cyber AI newsletter here. We break stories like this before they hit the headlines.
To understand the gravity of this issue, let’s first define what a Telegram zero-day vulnerability entails and why it poses such a significant threat.
What Is a Telegram Zero-Day Vulnerability?
A Telegram zero-day vulnerability refers to an unpatched Telegram security flaw in the Telegram app that is unknown to its developers and security teams. Because these bugs are undisclosed and unmitigated, attackers can exploit them in real time while the target remains defenseless. In high-risk communications platforms, such messaging app vulnerabilities are extraordinarily valuable, both economically and strategically.
Defining Zero-Day Vulnerabilities
By definition, a zero-day is a software vulnerability that has been discovered but not yet disclosed to the vendor. The developer has had “zero days” to fix it. Because no patch exists, there are no defenses in place against exploitation. This makes zero-days a preferred tool for high-stakes cyberattacks, including those carried out by nation-states, criminal syndicates, and advanced persistent threat (APT) groups.
Zero-day exploits are typically developed using advanced techniques such as reverse engineering, fuzz testing, or binary analysis. While many are sold quietly in private, others are now monetized through aggressive zero-day bounty programs, state-aligned bounty programs like Operation Zero, which offer multi-million-dollar rewards for reliable, exclusive, weaponizable exploits.
How Zero-Days Apply to Messaging Apps
Messaging apps are one of the most sensitive categories of software in the world. They carry communications between journalists and sources, dissidents and organizers, or even diplomats and government staff. A zero-day vulnerability in a messaging app like Telegram can result in:
- Remote Code Execution (RCE), enabling attackers to install and run malicious software on a target’s device.
- Account Hijacking, allowing impersonation, blackmail, or unauthorized access to conversations and files.
- Silent Data Exfiltration, where messages, photos, contacts, and metadata are extracted without the user’s knowledge.
Because Telegram’s infrastructure stores most data in the cloud by default, these Telegram security flaw exploits don’t always require breaking into a user’s device. Exploiting Telegram’s backend access and encryption model can be enough to compromise a user’s communications at scale.
Telegram’s Exposure to Zero-Click Attacks
Perhaps the most dangerous class of zero-day exploit is the zero-click attack. In these scenarios, users do not need to click, tap, or open anything for the exploit to succeed. Simply being online, or receiving a malicious message or file, may be enough to trigger a compromise.
Operation Zero’s bounty system explicitly prices zero-click exploits at $1.5 million, with full-chain, zero-click device takeovers commanding the full $4 million reward. Full-chain means the attack can start in Telegram, then escalate to full control of the device’s operating system, cameras, microphones, or storage.
This makes Telegram zero-day vulnerabilities especially attractive in authoritarian regimes. Surveillance of journalists, dissidents, opposition leaders, or even foreign diplomats becomes vastly easier when attackers don’t need physical access or user interaction. Given Telegram’s widespread use in countries like Iran, Russia, and Ukraine, its exposure to zero-click attacks and Telegram privacy concerns has become a frontline cybersecurity issue.
The unprecedented $4 million bounty underscores the strategic importance of these vulnerabilities. Let’s examine who is behind this offer and what it signals about Telegram’s role in global cyberwarfare.
The $4M Bounty: What It Means and Who Offered It

The announcement of a $4 million reward for a Telegram zero-day vulnerability, a critical exploit, was not part of a covert leak or speculative blog post. It was a public and deliberate statement issued by Operation Zero, a Russian-based exploit broker that specializes in purchasing and selling high-end offensive cybersecurity tools. The Telegram bounty appeared on their official site and was quickly confirmed by multiple security intelligence sources.
The size and visibility of this bounty serve two purposes. First, it reflects Telegram’s elevated strategic value in global surveillance and cyberwarfare. Second, it signals to elite exploit developers that Operation Zero is willing to pay more than Big Tech, including Apple and Google, for high-grade messaging app vulnerabilities. Telegram, a platform with a global user base, has officially entered the realm of state-level intelligence targeting.
Who Is Operation Zero?
Operation Zero is not a conventional bug bounty platform. It does not operate in coordination with software vendors, nor does it disclose vulnerabilities to developers for remediation. Instead, it exists to acquire exclusive, unreported exploits and resell them, often to state-aligned actors.
According to Security Affairs, Operation Zero, a leader in zero-day bounty programs, explicitly prioritizes zero-click, full-chain exploits, particularly those capable of bypassing both application-level and OS-level security layers. Its clients are believed to include Russian government agencies and intelligence groups looking to gain stealth access to foreign communication infrastructure.
Unlike Apple’s official Security Bounty, which tops out at $2 million for severe iOS vulnerabilities, Operation Zero offers twice that amount. It also comes with fewer restrictions, no vendor coordination, and significantly higher geopolitical stakes.
Bounty Structure and Exploit Categories
The published bounty for Telegram is structured in three escalating tiers:
- $500,000 for a one-click exploit, where minimal user interaction (such as opening a file or image) is required.
- $1.5 million for a zero-click exploit, which requires no user interaction at all.
- $4 million for a full-chain zero-click exploit, which provides root access to the operating system through Telegram alone.
By offering these figures, Operation Zero is making it clear that vulnerabilities in messaging apps, especially ones like Telegram that lack default end-to-end encryption, are more than just technical assets. They are political weapons.
State-Level Buyers and Espionage Value
Telegram is uniquely situated in a geopolitical grey zone. It is headquartered in Dubai, used heavily across Eastern Europe, and relied on in conflict zones from Ukraine to Iran. That makes it especially valuable for state-level surveillance operations.
The Ukrainian government banned Telegram, raising Telegram privacy concerns, on official devices in 2024, citing credible risks of espionage and disinformation dissemination. This decision was influenced in part by Telegram’s opaque encryption policies and repeated use in psychological operations campaigns during wartime.
Operation Zero’s buyer base is widely believed to include Russian intelligence services, who use zero-day bounty programs not only to develop cyber tools but also to deny those tools to rival states. By purchasing Telegram security flaw exploits exclusively and offering high bounties, Russia and its allies can ensure access remains asymmetric.
This demand has broader consequences. Messaging app vulnerabilities that used to circulate in academic or white-hat spaces are now directly monetized by shadow markets aligned with authoritarian governments. And with Telegram being the messaging app of choice for over 900 million users, the ripple effects of even a single unpatched flaw could be global.
For a broader look at how these tactics tie into state-sponsored AI and cyberwarfare strategy, we explore similar patterns in AI-Powered Cyberwarfare in 2025: The Global Security Crisis You Can’t Ignore, which outlines how military and intelligence actors are leveraging emerging technologies across digital fronts.
The high value placed on Telegram exploits is closely tied to its architectural weaknesses, which create multiple entry points for attackers. Let’s explore why Telegram’s design makes it such a prime target.
How Telegram’s Architecture Leaves It Exposed
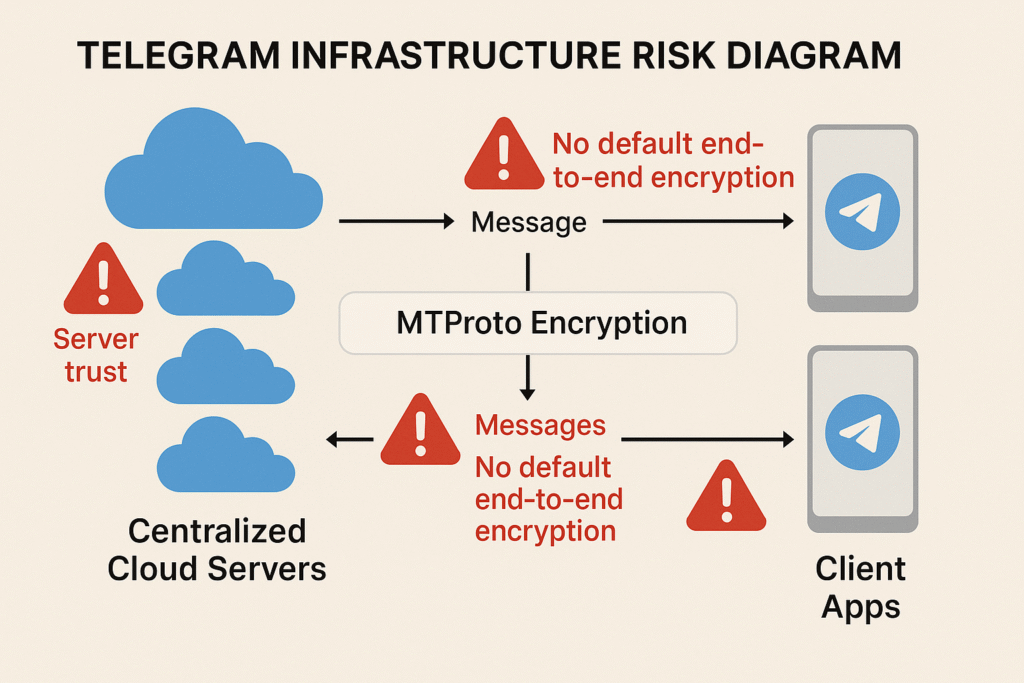
The Telegram zero-day vulnerability market exists not just because of the app’s popularity, but because of its architectural design choices, choices that expose a Telegram security flaw compared to more privacy-focused competitors. Despite its reputation as a secure platform, Telegram’s encryption policies, raising Telegram privacy concerns, server structure, and chat configuration create multiple potential attack surfaces, especially in the context of zero-day bounty programs like Operation Zero’s.
Centralized Cloud Servers and Default Encryption Gaps
Telegram does not use end-to-end encryption by default. Instead, the majority of user messages are stored in the cloud on Telegram’s own servers. While Telegram claims these messages are encrypted in transit and at rest, they are ultimately accessible to the service itself through key management that Telegram controls.
This is a major deviation from the models used by platforms like Signal, where messages are encrypted from sender to recipient, and even the platform cannot access content. On Telegram, only one-on-one “Secret Chats” are end-to-end encrypted, and even then, users must manually activate that mode. Group chats, channels, bots, and all synced messages use Telegram’s cloud-based MTProto protocol, which stores and processes data on centralized servers).
This cloud-first model introduces several risks:
- Messages are decryptable by Telegram, theoretically allowing internal or coerced access by government actors.
- Attackers only need to breach server infrastructure to access thousands, or millions, of message histories.
- Any Telegram zero-day vulnerability in cloud sync or encryption handling opens up exposure at a massive scale.
In practice, this means that a Telegram zero-day vulnerability does not always require breaching the user’s device. It may be enough to intercept or exploit a Telegram security flaw in how Telegram manages messages and encryption keys on its own servers.
MTProto 2.0 Protocol: Formally Verified but Trust-Based
Telegram uses its own proprietary encryption scheme, MTProto 2.0, to secure messages. While the protocol has been formally verified by independent researchers for confidentiality and forward secrecy arXiv, the key caveat is this: MTProto assumes the Telegram server is trusted.
This assumption creates a structural flaw. Unlike open-source, decentralized protocols where the user controls the encryption keys, Telegram handles encryption server-side for all non-secret chats. Researchers have warned that even with strong cryptography, any system that requires trust in the service provider opens itself up to man-in-the-middle attacks or coercive pressure from governments.
Key points about MTProto 2.0:
- It supports encryption at rest and in transit, but not full E2E in most configurations.
- Verification of the protocol doesn’t guarantee secure implementation.
- It has limited peer-reviewed transparency, as Telegram has not open-sourced its server code.
These characteristics make Telegram more difficult to audit externally and more vulnerable to messaging app vulnerabilities and zero-day exploits that target its server interactions.
Lack of End-to-End Encryption for Groups and Cross-Device Sync
One of the most critical weaknesses in Telegram’s architecture is its lack of end-to-end encryption for group chats and synced messages. Telegram allows users to install the app on multiple devices and instantly access all chat history. This convenience comes at a cost: true end-to-end encryption is not possible when messages must be stored and replicated across multiple device sessions via the cloud.
This setup introduces several key vulnerabilities:
- Group chats are never end-to-end encrypted, making them attractive targets for both state surveillance and criminal exploitation.
- Cross-device syncing requires Telegram to decrypt and re-encrypt messages, introducing multiple points of potential failure.
- Zero-day exploits can be leveraged server-side to intercept group communications at scale without alerting users.
As a result, even users who believe they are using Telegram securely may be unknowingly exposed. Telegram’s flexibility and usability come at the expense of structural privacy, amplifying Telegram privacy concerns, a tradeoff that exploit brokers are increasingly capitalizing on.
This design is a sharp contrast to platforms like Signal, where group chats and message sync are still fully encrypted and where the app architecture does not require trusting a third party with encryption keys. If you’re navigating high-risk communications, understanding this distinction is critical.
These architectural flaws amplify the real-world consequences of a Telegram zero-day vulnerability. Here are five critical risks that highlight the severity of this threat.
5 Disturbing Risks from the Exploit
The $4 million Telegram zero-day vulnerability bounty is not just a technical challenge for elite hackers. It represents a real and immediate threat to global privacy, democracy movements, journalism, and organizational trust. When attackers can compromise Telegram without user interaction, the consequences are far-reaching and potentially devastating. The risks are not hypothetical. They are already playing out in regions where Telegram use is common and state-aligned surveillance programs are active.
Mass Surveillance of Journalists and Activists
Telegram is often used in high-risk environments because it is perceived as secure. Activists in Iran, Ukraine, and Belarus have relied on the app to organize protests and communicate securely. However, this trust may be misplaced.
In 2024, the Ukrainian government banned Telegram on all official devices, citing clear evidence that vulnerabilities in Telegram, coupled with Telegram privacy concerns, could allow Russian intelligence to track conversations, locations, and plans of key individuals. This policy shift was driven by concerns that vulnerabilities in Telegram could allow Russian intelligence to track conversations, locations, and plans of key individuals.
For journalists, the implications are equally serious. A single zero-click Telegram exploit could compromise the phone of a reporter covering corruption or war crimes, exposing sources and sensitive documents. The same attack could be used against human rights defenders, whistleblowers, or foreign service personnel operating in conflict zones.
Device Root Compromise and Malware Delivery
Operation Zero, through its zero-day bounty programs, is offering $4 million specifically for full-chain Telegram zero-day exploits. This level of vulnerability allows an attacker to start within the Telegram app and escalate to full control of the target’s device. Once this type of root-level access is achieved, the attacker can:
- Activate microphones or cameras
- Log keystrokes, passwords, and biometric data
- Capture all app communications, not just Telegram
- Install persistent malware that survives reboots
This goes far beyond chat surveillance. It turns the victim’s phone into a tool of the attacker. And because zero-click delivery mechanisms are prized, victims may never know they’ve been compromised.
Telegram’s centralized server model also means that a Telegram security flaw in file processing or media preview features can potentially be exploited to deliver malware without user action.
Hijacked Accounts for Disinformation Campaigns
When Telegram accounts are compromised, attackers can hijack the identity of the user. For influencers, journalists, or activists, this opens the door to coordinated disinformation attacks.
A compromised account could be used to:
- Spread false political statements or endorsements
- Leak fabricated documents under the user’s name
- Disrupt organizing efforts by sending fake messages in group chats
- Undermine trust between real users in activist networks
We explored similar tactics in our post on Mobile Data Privacy Risks: 7 Shocking Facts You Didn’t Know.
Undermining Trust in Messaging Apps
Every time a platform like Telegram is exploited, public confidence in encrypted messaging as a whole is eroded. For users who depend on these tools for personal safety or professional security, repeated breaches can lead to confusion, despair, or fatal delays in switching platforms.
When vulnerabilities are left unpatched or hidden from the public, as is often the case with zero-day exploits sold through private bounty programs, users continue to trust tools that may no longer be safe.
This erosion of trust is especially dangerous in authoritarian contexts, where switching to less accessible apps may not be feasible. In those environments, Telegram’s perceived security can become a false shield.
Escalating Demand in Exploit Markets
The Operation Zero bounty reflects a broader trend: zero-day bounty programs are becoming more lucrative and more strategic. Telegram’s value in these markets is not just about financial gain. It’s about power.
By incentivizing developers to find and sell messaging app vulnerabilities privately, these programs:
- Shift security research away from public disclosure and toward exclusive state use
- Deny vulnerabilities to defenders who could patch them
- Create exploit monopolies, where one state actor has the means to compromise millions of users undetected
The rise in exploit value, especially for messaging app vulnerabilities, mirrors patterns we’ve tracked in broader cyberwarfare markets. This growing demand is also addressed in AI Cyberattacks Are Exploding: Top AI Security Tools to Stop Deepfake Phishing & Reinforcement Learning Hacks in 2025, which highlights how AI and cyberweapon markets are converging.
These risks are compounded by Telegram’s history of security lapses, which reveal a pattern of vulnerabilities that make it a prime target for exploit brokers.
Telegram’s Track Record on Privacy and Security
While Telegram has branded itself as a privacy-forward platform, its track record reveals a pattern of design choices, overlooked vulnerabilities, and limited transparency, raising Telegram privacy concerns, that challenge that perception. The rise in Telegram zero-day vulnerability bounties did not appear in a vacuum. Over the past several years, researchers have flagged serious cryptographic issues, real-world compromises, and a Telegram security flaw in Telegram’s overall approach to user security.
Past Vulnerabilities in MTProto
Telegram’s proprietary encryption protocol, MTProto, has been the subject of extensive scrutiny. In 2021, researchers from ETH Zurich and Royal Holloway, University of London identified four cryptographic vulnerabilities in Telegram’s earlier versions of the MTProto protocol. These flaws did not directly enable message decryption, but they exposed weaknesses in how Telegram handled authentication and session setup. These are issues that could have undermined the confidentiality and integrity of communications under certain conditions.
Telegram responded to some of these findings by releasing updated protocol versions and claiming that no practical exploits existed in the wild. However, the research community remained concerned. Telegram’s decision to use a homegrown protocol, rather than adopting widely vetted standards like Signal Protocol, remains controversial. Security experts generally view proprietary encryption as more vulnerable to an undiscovered Telegram zero-day vulnerability.
Even Telegram’s updated MTProto 2.0, while formally verified for key exchange security and forward secrecy, still relies on the assumption that Telegram’s servers are trustworthy, a foundational limitation we addressed in the previous section.
SIM Swap Account Hijacks Across Multiple Countries
Beyond theoretical flaws, Telegram has suffered real-world compromises, including messaging app vulnerabilities, that expose its systemic weaknesses. One of the most common and damaging attack vectors has been SIM swap hijacking, where attackers impersonate users to telecom providers and seize control of their phone numbers.
Once a SIM swap is successful, Telegram accounts can often be accessed immediately, especially if two-factor authentication (2FA) is not enabled or is reliant on SMS. This method has been used in:
- Russia, to compromise opposition figures and journalists
- Iran, where Telegram was already under scrutiny for being a tool of dissent
- Germany, during phishing and identity theft operations targeting politicians and activists Wikipedia)
These attacks bypass app-layer security altogether, exploiting Telegram’s reliance on phone numbers and SMS for account verification.
Malware Distributed via Telegram File Transfers
Telegram’s file-sharing features have also been weaponized to deliver malware. In mid-2024, cybersecurity researchers at ESET uncovered a Trojan campaign that embedded malware in seemingly benign Telegram file transfers, specifically targeting users in Eastern Europe.
The malware exploited Telegram’s content preview functionality to activate upon delivery, without requiring the recipient to open or download the file explicitly. While Telegram claimed the platform itself was not compromised, the incident showed how attackers can exploit Telegram’s flexibility and cloud-based architecture to deliver advanced persistent threats.
Unlike more restrictive platforms that scan for known malware signatures before allowing transfers, Telegram’s commitment to “user freedom” may expose a Telegram security flaw to creative abuse.
Transparency and Audit Concerns
Telegram’s entire infrastructure is largely closed to external audit. While the MTProto protocol has been partially published and formally analyzed, Telegram’s server code remains proprietary. This opacity stands in stark contrast to platforms like Signal, which not only publish their full source code but also undergo regular independent security audits.
This lack of transparency creates several problems:
- Researchers cannot verify how Telegram implements encryption in practice
- Users cannot be sure what data is stored, when, or under what conditions it may be accessed
- Exploits like those sought in the Operation Zero bounty may exist for months or years without public detection
Telegram’s refusal to implement default end-to-end encryption in all chats, combined with its limited third-party review, is a major reason why it remains a top target for exploit buyers and government surveillance programs.
Given these vulnerabilities, users must take proactive steps to safeguard their communications on Telegram or consider alternatives.
What You Can Do to Protect Yourself
The rising threat of a Telegram zero-day vulnerability is not something users can ignore, especially if they operate in high-risk environments with Telegram privacy concerns. While the average person may not be targeted by $4 million exploits, the same Telegram security flaw can still be used in mass surveillance, phishing, or disinformation campaigns. Fortunately, there are specific and actionable steps you can take to mitigate exposure on Telegram; or avoid it altogether.
Enable Secret Chats for End-to-End Protection
One of the most important distinctions in Telegram’s architecture is that only Secret Chats are end-to-end encrypted. These chats are encrypted directly between devices, meaning not even Telegram can read the content. However, this feature is not enabled by default and only works for one-on-one conversations, not groups or channels.
To use Secret Chats:
- Open a new message with a contact
- Tap on their profile and select “Start Secret Chat”
- Messages in this chat will not be synced across devices and will include optional self-destruct timers
Limitations:
Secret Chats cannot be used on Telegram Web, and any communication on public channels, groups, or bots will still go through Telegram’s cloud servers. If you’re depending on Telegram for privacy or whistleblower activity, this distinction is crucial.
Avoid SMS Verification and Use Strong 2FA
Telegram accounts are tied to phone numbers, and by default, the app allows login verification via SMS codes. This exposes users to SIM swap attacks, a well-documented and frequently exploited tactic that allows attackers to hijack a phone number by social engineering a telecom provider.
To reduce this risk:
- Enable Two-Step Verification inside the Telegram settings
- Choose a strong, unique password for the second verification layer
- Avoid linking your Telegram account to other apps or cloud services that use SMS
Whenever possible, avoid relying solely on SMS for security. If Telegram supported app-based or hardware security keys, that would be ideal; but until then, a strong password is your best secondary protection.
Keep All Apps and Systems Fully Updated
Zero-day vulnerabilities are, by definition, unpatched. However, once discovered, developers typically race to push out fixes. Running outdated versions of Telegram or your operating system can expose messaging app vulnerabilities to known Telegram zero-day vulnerability exploits that may already be circulating in attacker communities.
Recommendations:
- Enable automatic updates on your phone and desktop
- Frequently check for Telegram updates manually if using sideloaded versions
- Avoid using Telegram from unofficial clients or modded APKs, which may be out of date or include malicious modifications
This simple habit is one of the most effective defenses against exploitation through zero-day bounty programs. Exploits sold for millions today may become publicly weaponized in underground forums weeks or months later.
Evaluate Alternatives Like Signal or WhatsApp
If you are in a sensitive role, such as a journalist, activist, government worker, or cybersecurity researcher, consider transitioning to platforms that use default end-to-end encryption across all communication types.
Signal is widely regarded as the gold standard. It offers:
- End-to-end encryption by default
- Open-source, peer-reviewed code
- Group messaging and calls with the same encryption guarantees
- Minimal metadata collection
WhatsApp, while owned by Meta, also uses the Signal Protocol for message encryption. Although its metadata handling has raised concerns, it still provides stronger technical guarantees than Telegram in terms of default message confidentiality.
If you’re unsure which tools are right for your threat profile, we recommend reading our companion post on AI Cyberattacks Are Exploding: Top AI Security Tools to Stop Deepfake Phishing & Reinforcement Learning Hacks in 2025, which outlines vetted digital security products for high-risk use cases.
To receive more tool reviews and strategic cybersecurity briefings like this, subscribe to the Quantum Cyber AI newsletter for weekly insights on threat evolution, software audits, and digital defense strategies.
While individual actions can reduce risk, the Telegram zero-day bounty highlights broader systemic issues in the messaging app ecosystem that demand attention.
The Bigger Picture: What This Says About Messaging App Security
The $4 million bounty for a Telegram zero-day vulnerability, a critical exploit, is more than just a headline. It reflects a deeper truth about the current state of encrypted communication: design choices matter more than branding. Messaging apps like Telegram are not all created equal, and the architecture that underpins them directly determines their resilience, or Telegram security flaw, in the face of exploitation.
This moment should serve as a wake-up call for users, developers, and regulators alike. The economics of exploitation, combined with architectural weaknesses and geopolitical incentives, are reshaping how secure messaging functions in practice.
The Economic Incentives Behind Messaging Exploits
The exploit economy, fueled by zero-day bounty programs, has gone global; and it’s not just Western intelligence agencies or white-hat researchers driving it anymore. Exploit brokers like Operation Zero are now offering more than any traditional bug bounty platform, luring top-tier exploit developers into closed, exclusive deals with state actors.
The $4 million bounty for a full-chain Telegram exploit far exceeds Apple’s maximum $2 million payout for iOS bugs, despite Telegram being just one application. This signals a major market shift where apps with flawed architectures, and large user bases, have become lucrative targets for government surveillance programs and commercial espionage.
As these bounties increase, so does the danger. Messaging app vulnerabilities are not being disclosed to app developers or patched. They are being bought, hoarded, and deployed in silence.
Why Architecture Matters More Than Marketing
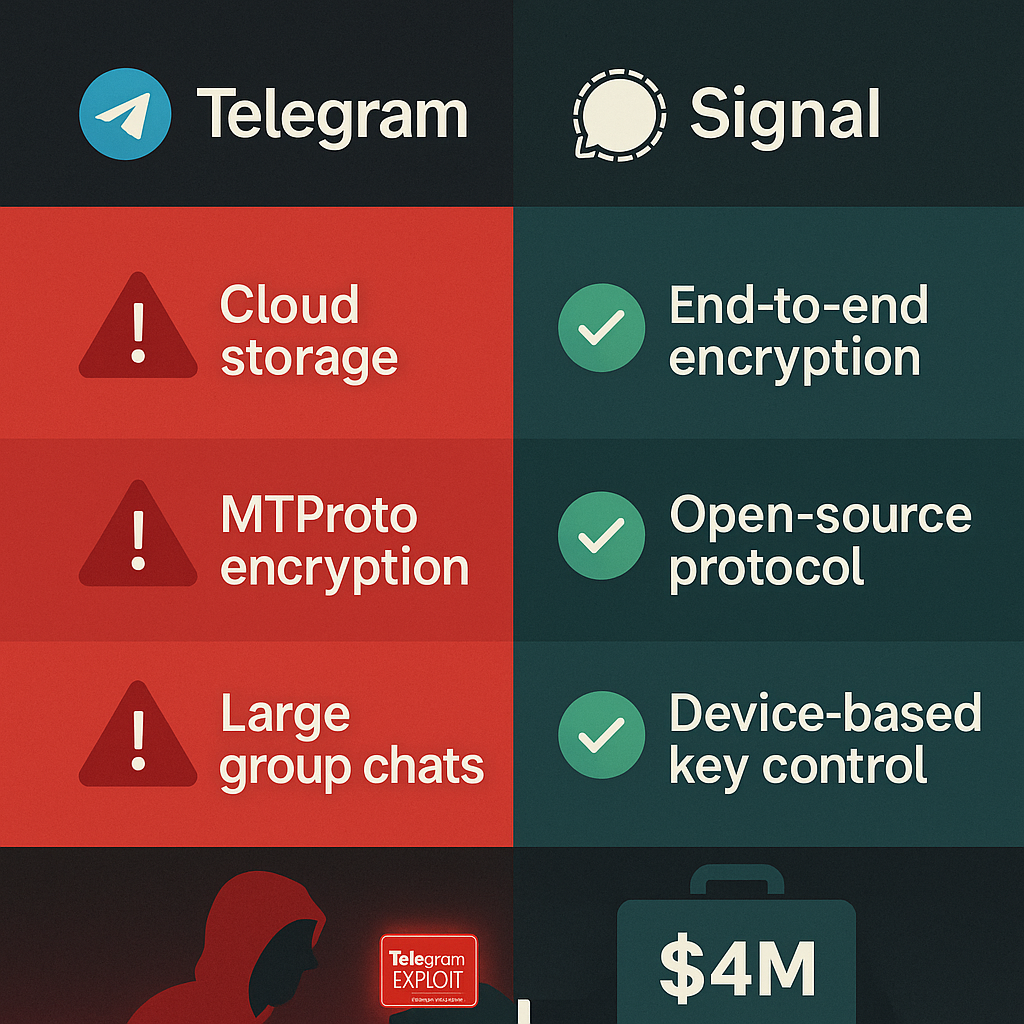
Telegram has cultivated a reputation as a secure app, but its technical architecture, raising Telegram privacy concerns, undermines that claim. As explored earlier, the app does not use end-to-end encryption by default, stores messages on its own servers, and uses a proprietary encryption protocol that requires trust in Telegram’s infrastructure.
Compare that to apps like Signal, which use:
- Open-source, widely peer-reviewed encryption protocols
- End-to-end encryption for all messages and calls by default
- Minimal metadata retention
- A zero-trust design model that assumes infrastructure will fail
This architectural difference is not just academic. It defines how likely an app is to withstand zero-day exploitation. Telegram’s choice to prioritize convenience, cloud sync, and broad accessibility has made it inherently more exploitable.
Lessons for Signal, WhatsApp, and Future Platforms
The Telegram zero-day vulnerability spotlight offers a roadmap for other platforms. Even apps with strong encryption protocols can become compromised if their implementation or default configurations introduce attack surfaces.
Key lessons include:
- Make end-to-end encryption the default, not an optional feature
- Avoid centralized message storage, especially without user-controlled keys
- Publish full server code to enable third-party audits and transparency
- Limit metadata retention to reduce the intelligence value of compromise
Apps like WhatsApp have made progress by adopting the Signal Protocol, but questions remain about how much data Meta retains and how that data could be subpoenaed, scraped, or intercepted.
For any new messaging platform entering the market, privacy and security cannot be bolted on later. They must be baked into the system design from the start.
Calls for Regulatory and Transparency Standards
The exploit market is growing faster than the regulatory frameworks that could help contain it. Messaging platforms are not subject to consistent global standards for encryption, data retention, or breach disclosure. And in the absence of transparency, users are forced to make decisions based on branding and word-of-mouth; often with fatal consequences in authoritarian regimes.
A coordinated response is needed. This could include:
- Mandating open-source encryption protocols for any app claiming to be private
- Requiring disclosure of known breaches, especially those exploited at scale
- Establishing international norms around zero-day exploit sales and bounty transparency
Until these norms exist, private sector developers, journalists, and activists will remain vulnerable to the silent but growing threat of commercialized cyberweapons.
We unpack the wider state of this ecosystem further in AI-Powered Cyberwarfare in 2025: The Global Security Crisis You Can’t Ignore, which connects the rise in messaging app exploits to broader state-level information warfare campaigns.
The Telegram zero-day bounty is a stark reminder of these challenges, pointing to an urgent need for both immediate action and long-term reform.
Conclusion & Future Outlook
The revelation that a Telegram zero-day vulnerability is worth $4 million on the open market should shatter any lingering illusions about the security of popular messaging apps. Telegram’s reputation for privacy has never been backed by strong technical defaults, and its architecture, centered around cloud storage, centralized key handling, and optional encryption, raising Telegram privacy concerns, has become an exploitable goldmine for hostile actors.
This is not just a Telegram problem. It’s a systemic Telegram security flaw in how we evaluate digital tools. Users assume apps that say they are encrypted are secure. But security is not a marketing promise. It’s a function of architectural design, encryption protocols, and transparency in implementation. Telegram fails on multiple counts.
The stakes are rising. Exploit brokers like Operation Zero are industrializing the vulnerability market, turning security research into geopolitical weapons. Intelligence agencies, authoritarian regimes, and even private contractors now have access to tools that once required years of state-level investment to develop. And with cloud-first platforms like Telegram, a single Telegram zero-day vulnerability can compromise millions of devices silently.
Looking forward, the path to protecting users must be multi-pronged:
- Messaging platforms need to adopt end-to-end encryption by default, with no exceptions for group chats, synced messages, or convenience features.
- Regulators should push for transparency and security standards, especially around encryption and metadata retention.
- Users must become more discerning, choosing tools like Signal that prioritize security over growth or UI gimmicks.
If you work in policy, cybersecurity, journalism, or high-risk activism, do not assume the apps you use are safe simply because they are popular. Scrutinize the infrastructure. Follow the exploit markets. And demand accountability from developers who build tools used by hundreds of millions of people.
To stay ahead of emerging threats like these, and to receive expert breakdowns of cyberwarfare tactics, AI surveillance risks, and global exploit trends, subscribe to the Quantum Cyber AI newsletter. We cover what others miss, before it becomes a breach.
Key Takeaways
- Telegram zero-day vulnerabilities are now valued at up to $4 million, marking an unprecedented escalation in the messaging app exploit economy.
- Most Telegram chats are not end-to-end encrypted by default, making them significantly more vulnerable to both technical exploits and government surveillance, amplifying Telegram privacy concerns.
- Operation Zero’s public bounty structure confirms state-level demand for exploits capable of full device compromise through Telegram alone.
- Telegram’s architecture, reliant on centralized cloud storage and proprietary protocols, creates multiple attack surfaces not present in apps like Signal.
- Users can mitigate risk by enabling Secret Chats, using strong two-factor authentication, and considering alternatives like Signal for sensitive communications to address Telegram security flaw risks.
- The exploit market is outpacing regulation, and messaging apps must take proactive steps toward transparency, security audits, and encryption by default.
FAQ
Q1: Why is Telegram targeted more than Signal?
Telegram lacks default end-to-end encryption for most chats, stores messages on its own servers, and uses a proprietary encryption protocol that requires trusting Telegram’s infrastructure, increasing the risk of a Telegram zero-day vulnerability. Signal, by contrast, uses default E2E encryption, open-source code, and a zero-trust model.
Q2: What’s a full-chain exploit?
A full-chain exploit is a series of linked vulnerabilities that allow an attacker to move from compromising an app like Telegram to gaining full control over the device’s operating system, files, sensors, and communications.
Q3: Are Secret Chats in Telegram actually secure?
Secret Chats are encrypted end-to-end and provide more protection than regular Telegram chats. However, they only work for one-on-one conversations, are not available on all platforms (like web or desktop), and don’t support group functionality or device syncing.
Q4: Has Telegram responded to the $4 million bounty?
As of June 2025, Telegram has not issued a formal public statement addressing the Operation Zero bounty or the risks associated with a Telegram security flaw targeting its platform.
Q5: Should I stop using Telegram altogether?
If you’re handling sensitive, high-risk communication, such as in journalism, activism, or government work, switching to platforms like Signal is strongly recommended to avoid Telegram privacy concerns. Telegram can still be used for casual or non-sensitive interactions, but it should not be relied on for security-critical communications.
