In April 2025, cybersecurity firm iVerify published a report that should concern anyone who uses a mobile phone. Their investigation revealed that over 60 mobile operators across 35 countries, including close U.S. allies, are routing users’ sensitive mobile data through China’s state-owned telecommunications networks.
This isn’t a theoretical threat or a distant possibility. It’s happening right now, often without user knowledge or consent. Your call metadata, text messages, authentication codes, and location data may be flowing through infrastructure controlled by China Mobile, China Telecom, or China Unicom. These companies are legally required to cooperate with Chinese state surveillance.
Unlike a traditional data breach, there’s no notification. Unlike a phishing attack, there’s no warning. The exposure risk is quiet, continuous, and largely invisible until reports like iVerify’s bring it to light.
This investigation breaks down the full scope of the threat: how international data routing actually works, which countries and carriers are involved, the surveillance implications, and most importantly, what you can do to protect yourself.
To get weekly breakdowns like this on AI, cybersecurity, and digital privacy, subscribe to our newsletter here.
What iVerify Discovered About Mobile Data Routing
The iVerify team didn’t rely on speculation or theoretical models. They conducted systematic network traces, following the actual paths that mobile signaling traffic takes across international borders. What they discovered was empirical evidence that carriers across Asia, the Middle East, and Oceania were using Chinese state-controlled infrastructure to handle core mobile functions, revealing significant mobile data privacy risks.
The Role of Major Chinese Telecom Giants
The three major players at the center of this issue are China Mobile International, China Telecom Global, and China Unicom Global. These entities provide the interconnect services that link different national carriers together. When your local carrier lacks infrastructure in a particular region, it often leases capacity from these global providers, frequently without realizing the security implications or the resulting privacy threat.
Outdated Protocols: SS7 and Diameter Vulnerabilities
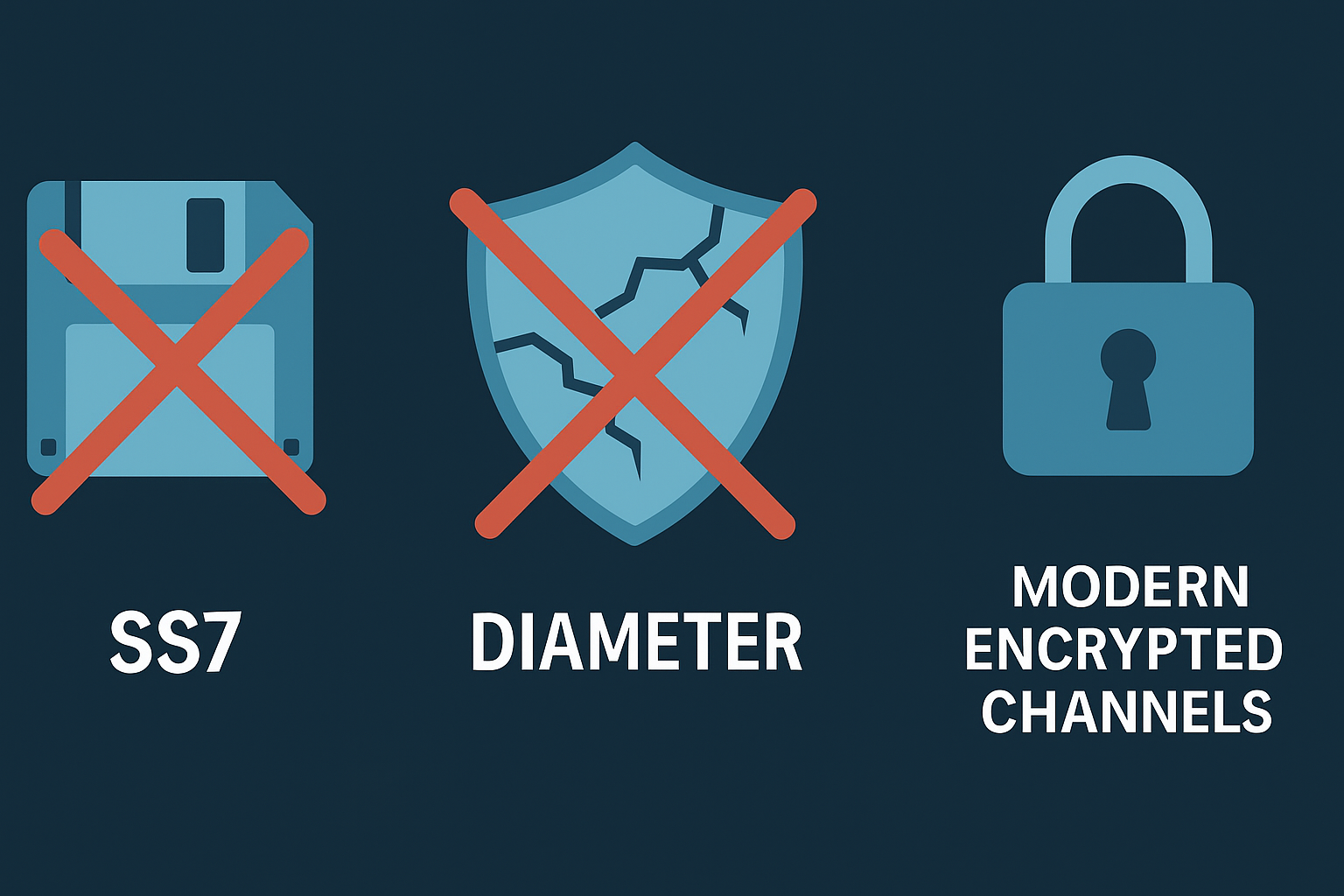
The technical foundation of this problem lies in outdated signaling protocols that predate modern security standards. SS7 (Signaling System No. 7) dates back to the 1970s, while Diameter was developed in the early 2000s. Neither was designed with encryption or privacy protection in mind, which creates a significant signaling-layer vulnerability.
These protocols handle critical mobile functions like authenticating users, routing messages, initiating calls, and tracking devices in real time. Because they lack encryption and verification, any network operator in the chain can potentially access or manipulate this data in transit. When those operators are legally required to cooperate with surveillance, as in China, the risk becomes systemic.
These vulnerabilities aren’t theoretical. Researchers have repeatedly demonstrated real-world attacks:
- In 2017, German telecoms confirmed SS7-based attacks that allowed hackers to intercept text messages for two-factor authentication.
- China’s state-owned telecom interconnect providers, including China Mobile International and China Telecom Global, leverage outdated and unencrypted signaling protocols like SS7 and Diameter. This infrastructure grants them direct access to sensitive mobile data, such as authentication details, SMS messages, and location updates, without user consent, posing significant global surveillance risks and further revealing the reach of the China surveillance internet.
These vulnerabilities are compounded by a lack of international enforcement. Telecom regulators vary widely by country, and there are no consistent global standards for routing transparency or security, which perpetuates mobile carrier privacy issues.
How Your Data Ends Up in Foreign Networks
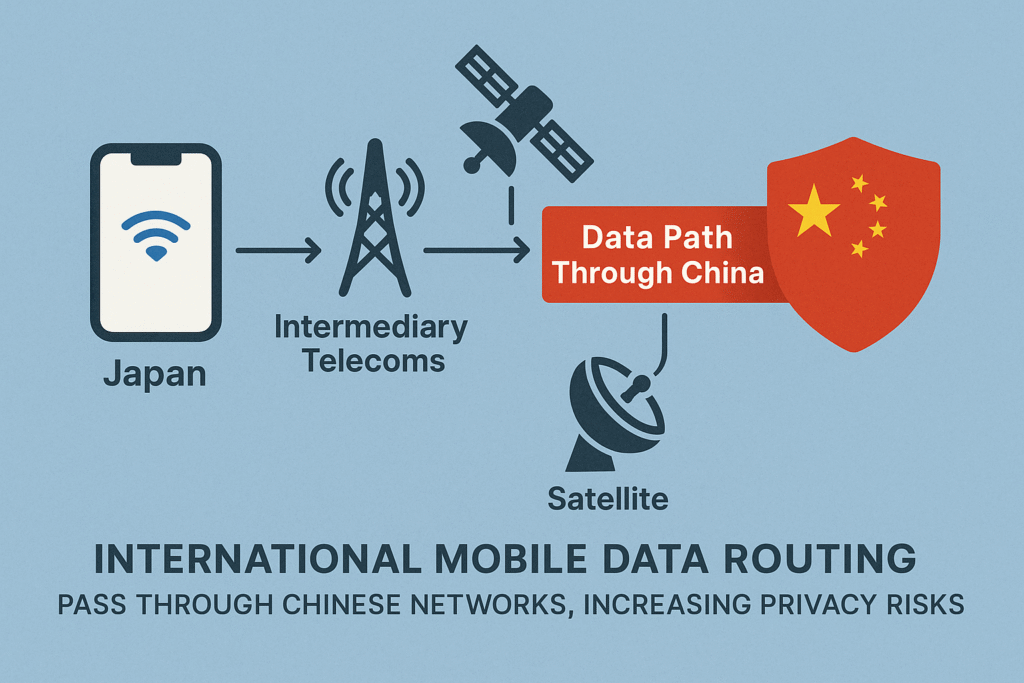
Many users assume their mobile data stays within their home country’s networks. The reality is far more complex. Global telecommunications operates on a web of interconnect agreements, where carriers lease capacity from whoever offers the most cost-effective or reliable routes. This often leads to unexpected cross-border data exposure.
The Role of Roaming and Interconnect Agreements
This affects more than just international travelers. iVerify found that users in countries like Japan, Saudi Arabia, and New Zealand had their signaling traffic routed through Chinese networks even during purely domestic communications. This happens due to interconnect agreements, where carriers lease capacity from global backbone providers who offer the cheapest or most available paths.
In some cases, telecoms may not even be aware that their upstream partners are using Chinese nodes. But the effect is the same: substantial increases in surveillance exposure when foreign infrastructure becomes part of the signal path. This highlights a pervasive problem with international data routing transparency.
Telecom Infrastructure Is Global and Opaque
Most users assume their mobile data takes a direct route from their phone to the nearest data center. In reality, mobile signaling traffic can cross oceans, touch multiple continents, and pass through networks governed by very different privacy laws before it arrives. Much of this international data routing is enabled by undersea cables, which link regional hubs together in a dense, often circuitous mesh.
Telecoms don’t always know, or admit, where this routing occurs. That opacity is a core feature of the system, not a bug. As iVerify points out, telecom operators often prioritize uptime and cost savings over privacy transparency. This inertia contributes significantly to mobile data privacy risks.
We cover stories like this in our newsletter, subscribe here for weekly briefings on hidden infrastructure risks, AI-driven exploits, and advanced cybersecurity defense.
The Privacy and Surveillance Risks Explained
Understanding the technical vulnerabilities in global mobile data routing is important, but the real concern lies in what those vulnerabilities enable: persistent, large-scale surveillance. When your mobile data passes through Chinese infrastructure, it is not just technically exposed, it is legally accessible to Chinese authorities. That combination of insecure transport and authoritarian control creates serious mobile data privacy risks with geopolitical consequences.
These mobile data vulnerabilities mirror the broader risk landscape seen in AI-Powered Cyberattacks on Critical Infrastructure: How Hackers Are Targeting Energy, Water & Banks in 2025, where state-linked access to networks can lead to catastrophic consequences across essential systems.
Chinese Law Requires Cooperation with Intelligence Agencies

Unlike in the U.S. or EU, Chinese companies are bound by the National Intelligence Law of 2017, which explicitly requires all organizations and citizens to support, assist, and cooperate with national intelligence work. This means any Chinese telecom handling your data is legally obligated to provide access to the government if requested. This legal framework transforms routine network infrastructure into a potent surveillance apparatus.
This isn’t a vague threat; it’s codified into law. If your mobile data passes through China surveillance internet infrastructure, it may be collected without your consent or knowledge, contributing to significant exposure risk.
What Data Can Be Collected in Transit
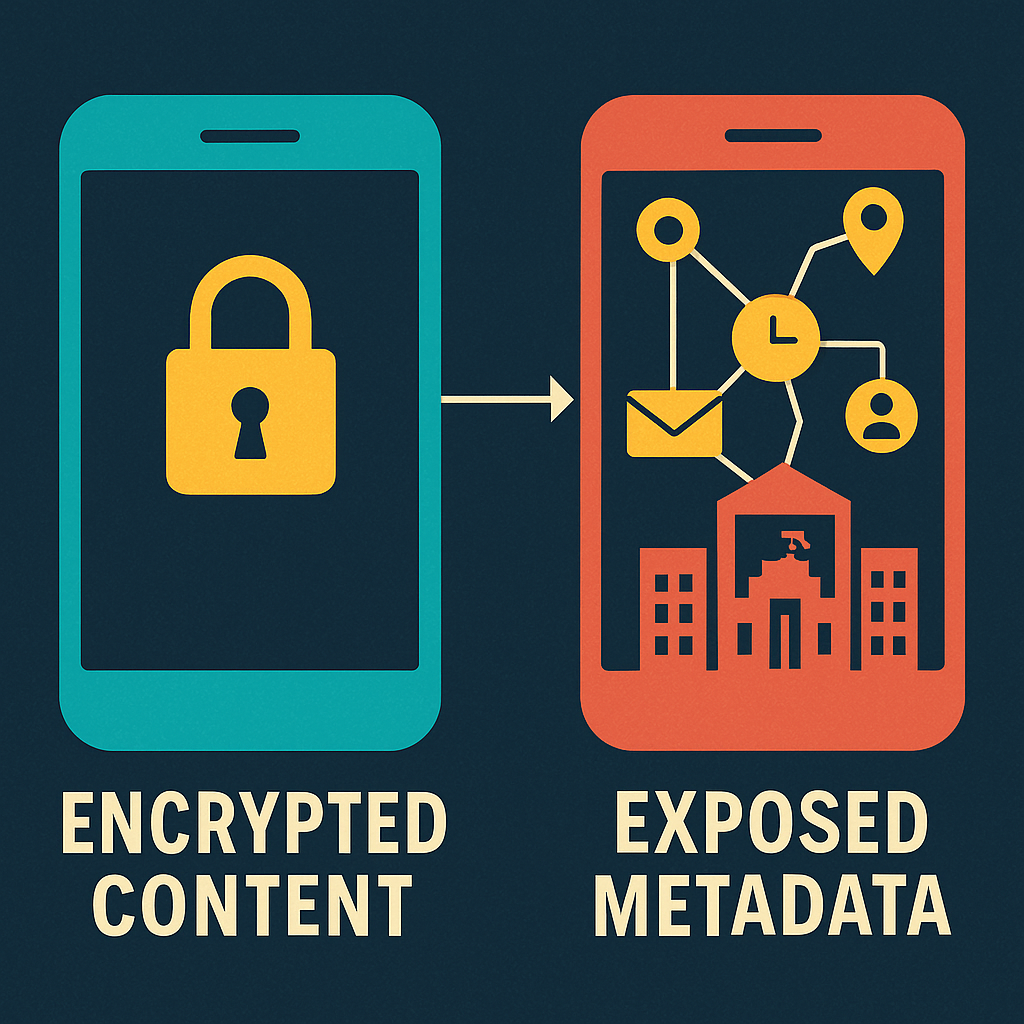
The unencrypted nature of protocols like SS7 and Diameter means that nearly every form of signaling data is readable by the network through which it passes. This includes:
- Subscriber identity information (IMSI): A unique identifier tied to your SIM card for tracking.
- Communication Metadata: Call records showing who you contacted, when, and from where; SMS delivery confirmations and routing information; duration and frequency patterns of communications.
- Location and Movement Data: Real-time location updates from cell tower connections; travel patterns and geographic movement over time; international roaming activity and destinations.
- Authentication Vulnerabilities: SMS-based two-factor authentication codes; mobile banking verification messages; account recovery and password reset communications.
The power of this metadata cannot be overstated. As former NSA General Counsel Stewart Baker observed: “Metadata absolutely tells you everything about somebody’s life.” When combined with China’s advanced data analysis capabilities, this information enables comprehensive profiling and tracking, increasing privacy threat.
Beyond Surveillance: Active Exploitation and Identity Theft
The security risks aren’t limited to passive surveillance. The signaling data that flows through these channels can be actively abused, significantly increasing mobile data privacy risks. For instance:
- Authentication bypass: Intercepted SMS codes can be used to access accounts like banks, email, or cloud storage.
- Call redirection: Traffic can be rerouted to enable man-in-the-middle attacks, going undetected by the end user.
- Identity spoofing: Compromised signaling data can be used to impersonate users.
- Account takeover: Combined metadata and authentication access enables comprehensive account control.
This kind of invisible interception represents one of the most serious mobile data privacy risks for business travelers and remote professionals, exposing them to significant cross-border data exposure. For businesses, the risk of espionage or account compromise via mobile signaling is a significant operational concern, particularly when operating abroad. The scope of this issue goes far beyond individual inconvenience; it’s a systemic surveillance concern embedded in the very infrastructure of the internet.
What Users Can Do to Protect Themselves
The scale of the problem may feel overwhelming, but individual users are not powerless. While you can’t control how telecom carriers route your signaling data, you can reduce your exposure to the most vulnerable pathways. Protecting your mobile data privacy begins with understanding which layers of your digital communication are at risk and which of these mobile data privacy risks are avoidable with user-level defenses against cross-border data exposure.
Use End-to-End Encrypted Apps (Signal, WhatsApp, ProtonMail)
Your first line of defense is end-to-end encryption (E2EE). If your messages, calls, or emails are encrypted from device to device, then even if the data flows through Chinese infrastructure, it cannot be decrypted midstream. This reduces the surveillance value of routing and mitigates mobile data privacy risks from China surveillance internet access.
Recommended E2EE tools include:
- Signal for messaging and voice/video calls.
- WhatsApp, which also supports strong E2EE for calls and messages.
- ProtonMail and Tutanota for secure email, especially for international communications.
These apps ensure that content exposure is prevented even when metadata (such as time or sender) remains visible.
Leverage VPNs, But Choose Wisely
A Virtual Private Network (VPN) encrypts your internet traffic from your device to the VPN’s server, masking your IP address and preventing snooping on data in transit. This is especially important when traveling or connecting to public networks, offering protection against cross-border data exposure.
However, not all VPNs are created equal:
- Avoid free VPNs or those based in surveillance-heavy jurisdictions.
- Use vetted services with transparent privacy policies and proven no-logs policies.
- Consider VPNs operated from jurisdictions with strong privacy laws (e.g., Switzerland, Iceland).
This tactic doesn’t protect signaling data (like SS7), but it does shield the content of your web traffic and apps. For example, if you’re using secure cloud services or online banking apps, a good VPN can protect you from cross-border data exposure in transit. This is a key step in managing mobile data privacy risks.
You can find more recommendations in our post on Shocking AI-Powered Cybersecurity Threats in 2025: Protect Yourself Against New Advanced Attacks, which highlights privacy tools in practical scenarios.
Disable Roaming and Manage App Permissions
One of the simplest and most effective ways to reduce signaling-layer vulnerabilities and mitigate mobile data privacy risks is to disable international roaming when it’s not needed. This prevents your device from connecting to foreign telecom infrastructure altogether, reducing cross-border data exposure.
Additionally, review your app permissions:
- Disable location tracking for apps that don’t require it.
- Restrict background data usage to trusted apps.
- Avoid SMS-based two-factor authentication in favor of authentication apps like Authy or Google Authenticator.
These steps can prevent your device from generating or exposing unnecessary data that could be intercepted during foreign routing. Taking control of how your device connects, even passively, is a critical way to reduce exposure risk.
Monitor Mobile Routing with iVerify or Similar Tools
To go a step further, consider using tools like iVerify that can alert you to unusual or insecure routing patterns related to international data routing. While not all users will understand how to interpret signaling data, these apps can detect suspicious behavior and provide guidance when issues arise, helping to pinpoint mobile data privacy risks.
iVerify specifically provides device hardening guidance and behavioral monitoring that can help detect network-level threats, even when they don’t trigger obvious red flags regarding cross-border data exposure. For businesses managing enterprise devices, incorporating mobile threat detection (MTD) platforms like Lookout or Zimperium can add a layer of protection across all employee endpoints, further addressing mobile data privacy risks.
These actions are not silver bullets, but they offer meaningful control over mobile data privacy risks, especially in an environment where the infrastructure itself is flawed and susceptible to China surveillance internet practices. For additional tips on safeguarding your connected life beyond mobile devices, check out our guide on How to Secure Your Smart Home from Hackers: The Ultimate Guide 2025.
Why Governments and Carriers Haven’t Acted
Given the seriousness of these surveillance concerns, one might expect sweeping reforms, international coordination, or at least some form of regulatory enforcement. But the global telecom industry operates in a gray zone, where outdated protocols meet cross-border jurisdictional limits, and geopolitical tensions discourage transparency. The result is a high-stakes problem with very few direct accountability mechanisms, which complicates addressing mobile data privacy risks and mobile carrier privacy issues.
Global Telecom Is a Fragmented and Legacy-Driven System
At the heart of the issue is infrastructure inertia. Telecom operators across the world still rely on legacy signaling protocols like SS7 and Diameter, despite their well-documented signaling-layer vulnerabilities. These protocols are deeply embedded in the global mobile ecosystem, especially for international roaming.
The problem isn’t just technical; it’s systemic. The business model of many mobile carriers depends on low-cost interconnects and flexible roaming partnerships, often with little regard for where or how the data is routed. Updating those systems would involve:
- Infrastructure modernization across thousands of global carriers.
- Redesigning interconnect contracts and peering relationships.
- Government involvement in defining secure-by-default signaling standards.
None of these are trivial tasks, and in an industry built on thin margins and massive scale, many carriers simply don’t see the incentive to prioritize security until forced by law or public pressure. Without coordinated modernization, mobile data privacy risks will continue to grow as international mobile traffic expands, amplifying the threat posed by the China surveillance internet.
No Global Rules for Cross-Border Routing
Perhaps the most striking gap is the lack of international governance around telecom routing. While data protection laws like the GDPR regulate data storage and processing, they don’t address how mobile signaling is routed between countries. There’s no equivalent to the GDPR for routing transparency or telecom infrastructure security, leading to persistent mobile carrier privacy issues.
This regulatory blind spot allows Chinese state-owned telecoms to act as transit providers for traffic from dozens of countries, without informing those countries, let alone their citizens. These networks can technically comply with local laws while still handing off traffic to infrastructure governed by Chinese surveillance laws, significantly increasing mobile data privacy risks and cross-border data exposure.
Political Sensitivities and Economic Dependence
Telecom policy isn’t just a technical issue; it’s a diplomatic one. Many of the nations identified in the iVerify report rely on China as a trading partner. In some cases, Chinese telecom companies have invested in local infrastructure or maintain long-term partnerships with domestic carriers, which can complicate addressing mobile carrier privacy issues.
Challenging these arrangements would require more than technical upgrades. It would involve disrupting business deals, straining diplomatic relationships, and confronting a global telecom industry that often prefers plausible deniability to accountability regarding cross-border data exposure and mobile data privacy risks. Even in the United States, where awareness of Chinese surveillance risks is high, telecom routing remains largely unregulated beyond voluntary standards. The FCC has focused on banning hardware from Chinese vendors like Huawei and ZTE, but hasn’t addressed the larger issue of international data routing via Chinese transit networks, perpetuating broader impact of the China surveillance internet on global telecom routing.
This gap is why issues like this persist, and why user vigilance is so important.
Conclusion and Future Outlook
What the iVerify report reveals is not just a technical vulnerability or an obscure network quirk; it’s a global failure of accountability. Your privacy doesn’t end at the border, and it doesn’t respect your choice of carrier. These vulnerabilities are embedded in the hidden infrastructure of international telecom, routed through jurisdictions where surveillance is not just legal, but required, directly contributing to cross-border data exposure and broader mobile carrier privacy issues.
We now know that more than 60 mobile operators in 35 countries have allowed sensitive mobile signaling data, including location updates, authentication protocols, and metadata, to pass through Chinese state-owned networks. Whether by negligence, cost-saving decisions, or infrastructural dependency, the result is the same: your data may be silently exposed to surveillance by an authoritarian regime via the China surveillance internet, escalating mobile data privacy risks.
Worse yet, these security vulnerabilities persist because they are profitable, difficult to detect, and politically inconvenient to challenge. Governments are often slow to act, especially when doing so means disrupting trade, telecom partnerships, or geopolitical relationships. Telecom carriers, for their part, have little financial incentive to scrutinize how traffic is routed through upstream partners.
The future will likely bring more scrutiny to these issues. Governments may begin requiring routing transparency reports. International standards may finally emerge to govern mobile signaling protocols. And security-conscious companies may start demanding clearer assurances from their telecom vendors regarding mobile data privacy risks and secure international data routing.
Until governments act, protecting yourself is no longer optional; it’s essential. As telecom threats grow more opaque and more political, digital self-defense must become second nature.
Key Takeaways
- Over 60 global carriers route mobile signaling data through Chinese state-owned telecoms, exposing user data to potential surveillance.
- This routing involves outdated, insecure protocols like SS7 and Diameter, which lack encryption and enable interception, contributing to mobile carrier privacy issues.
- Chinese law mandates telecom cooperation with government intelligence, legally enabling data collection in transit via the China surveillance internet.
- Countries affected include U.S. allies like Japan, South Korea, Saudi Arabia, and New Zealand, even when users aren’t roaming, increasing cross-border data exposure.
- Users can reduce exposure risk by using encrypted apps, disabling roaming, choosing strong VPNs, and monitoring device behavior with tools like iVerify.
- Governments and telecoms have largely failed to act due to infrastructure inertia, lack of global standards, and geopolitical complexity.
Frequently Asked Questions (FAQ)
Q1: How do I know if my mobile data is routed through China? Most users can’t detect this directly, but apps like iVerify can alert you to suspicious routing behavior. Additionally, your data may be exposed even without international roaming if your carrier relies on Chinese interconnect partners.
Q2: Does a VPN protect my signaling data? No. VPNs encrypt your internet traffic but not mobile signaling data like SS7 messages or location pings. However, they still help protect web activity and app communications from interception.
Q3: Is this surveillance legal? In China, yes, telecoms are required to cooperate with state intelligence. Internationally, it operates in a legal gray area due to the absence of clear global standards for routing transparency.
Q4: Are U.S. mobile carriers doing this? Not directly, but U.S. user data can still be routed through Chinese networks when roaming internationally or through app infrastructure that relies on global routing paths.
Q5: What’s the risk for businesses and professionals? High. Business travelers, journalists, diplomats, and executives are especially vulnerable to data interception, account compromise, or corporate espionage via signaling-layer surveillance.
