
Imagine this: It’s a regular Monday morning. Students log into their Chromebooks for class—only to find a flashing red screen. Files encrypted. Systems locked. A message demanding ransom in Bitcoin. The school goes dark. No internet. No email. No attendance system. No lunch accounts.
This isn’t fiction. It’s happening across America—and it’s getting worse.
Until recently, there was at least a slow march toward improving school cybersecurity. Agencies like CISA, the FBI, and the Department of Education had begun building a patchwork of best practices, alerts, and low-cost tools to help districts stay safe.
That progress is now gone.
🔥 Stay ahead of AI cyber threats. Sign up for our cybersecurity newsletter and updates here.
In 2025, as President Trump dismantles the Department of Education and guts CISA’s budget, America’s schools have been left to face rising cyberattacks alone.
Local leaders are being told to “do more with less”—even as ransomware attacks escalate, student data gets sold on the dark web, and districts with no cybersecurity staff are forced to rebuild their networks from scratch.
“We’re back to square one.”
— Doug Levin, K12 SIX, March 2025
And yet, the attacks are accelerating.
Cyberattacks on schools rose 92% between 2022 and 2023, with at least 98 confirmed ransomware attacks on K–12 institutions in 2023 alone.
Meanwhile, many districts still allocate less than 2% of their IT budgets to cybersecurity, and only one-third of U.S. schools have a full-time cybersecurity staffer [Cybersecurity Dive, 2023]. With no dedicated federal funding and E-Rate still refusing to cover cybersecurity tools, schools are on their own.
The result? A nationwide crisis—fueled by outdated infrastructure, missing personnel, and now, a total federal retreat.
👉→ Explore how AI cyberwarfare is shaping global and domestic threat landscapes.
🎯 Why Schools Are Prime Cyber Targets
Schools are perfect storm targets: underfunded, overexposed, and filled with sensitive data.
- Outdated Infrastructure: Many schools still run legacy systems from the 2000s, with no centralized patching or firewall protocols.
📎 Confirmed by the U.S. Government Accountability Office and CISA’s 2023 K–12 Cybersecurity Report (CISA, 2023). - No Dedicated Cybersecurity Staff: According to the Consortium for School Networking (CoSN), only 12% of school districts have a full-time cybersecurity position.
High-Value Data: Student records include names, Social Security numbers, addresses, medical info, and sometimes immigration status—making them prime black-market commodities.
📎 Confirmed by the U.S. Department of Education and Identity Theft Resource Center (ITRC)
“Schools are attractive targets because they have limited resources and valuable data.”
— Cybersecurity and Infrastructure Security Agency (CISA)
A 2023 report from the Center for Internet Security found that K–12 organizations were the single most targeted sector for ransomware that year.
Without adequate school cybersecurity protections, K–12 schools are vulnerable to ransomware attacks, identity theft, and long-term reputational harm.
👉→ See how AI malware is redefining what schools—and businesses—must prepare for.
💥 Real-World Attacks: A National Pattern Emerges

Let’s look at just a few high-profile cases of ransomware attacks and student data breaches over the last three years:
📍 Los Angeles Unified School District (2022)
One of the largest school districts in the country was hit with a ransomware attack that disrupted systems and exposed sensitive student information. Despite a swift response, hackers released 500GB of stolen data online, including student psychological assessments and disciplinary records.
📍 Iowa Public Schools (2023)
In January 2023, Des Moines Public Schools suffered a major ransomware attack that forced the district offline for two days, disrupting internet access and class operations. The attackers targeted student identity data and left a ransom note, though DMPS refused to pay. About 6,700 individuals were notified their personal data may have been exposed. The FBI and cybersecurity experts assisted in the response, and DMPS has since invested $4 million into strengthening its network security.
📍 Minneapolis Public Schools (2023)
In early 2023, Minneapolis Public Schools (MPS) experienced a significant ransomware attack. The Medusa ransomware group claimed responsibility, demanding a $1 million ransom, which the district did not pay. Subsequently, the attackers released over 300,000 files online, containing sensitive information such as student records, medical data, and reports on disciplinary incidents. The breach affected more than 100,000 individuals, leading MPS to offer free credit monitoring services to those impacted. This incident underscores the increasing vulnerability of educational institutions to cyber threats.
📍 Small, Rural Schools
It’s not just big districts. Small schools with only one IT staffer (or none) are now soft targets. In a survey conducted by StateScoop in late 2023, 67% of small districts said they had no written cybersecurity plan.
👉→ Learn how AI is targeting energy, water, and education systems alike.
📉 The Role of Budget Cuts in Escalating K–12 Cyber Threats

The gap between threats and school cybersecurity readiness is widening—especially as cybersecurity funding dries up. This funding gap leaves every district more exposed to sophisticated ransomware attacks. Cybersecurity funding in schools is declining—even as attacks increase. Why?
- Federal Tech Grants Have Stalled: Programs like E-Rate don’t cover cybersecurity software or staff, limiting how schools can protect against cyber threats.
COVID Relief Expired: Many schools used pandemic relief funding to upgrade devices—but did not receive ongoing support for cybersecurity once those funds expired. - Competing Priorities: School boards often prioritize visible needs—like HVAC, textbooks, or staffing—over “invisible” cyber risks.
“Most school districts report cost as the primary barrier to implementing stronger cybersecurity protections.”
According to a 2022 report by the Government Accountability Office (GAO), the loss of learning following a cyberattack ranged from 3 days to 3 weeks, and recovery time could take anywhere from 2 to 9 months. Furthermore, the same GAO report highlighted that school districts’ financial losses from cyber incidents can range from $50,000 to $1 million due to expenses caused by such events.
🧠 What’s at Stake: Student Privacy, Education Access, and Safety
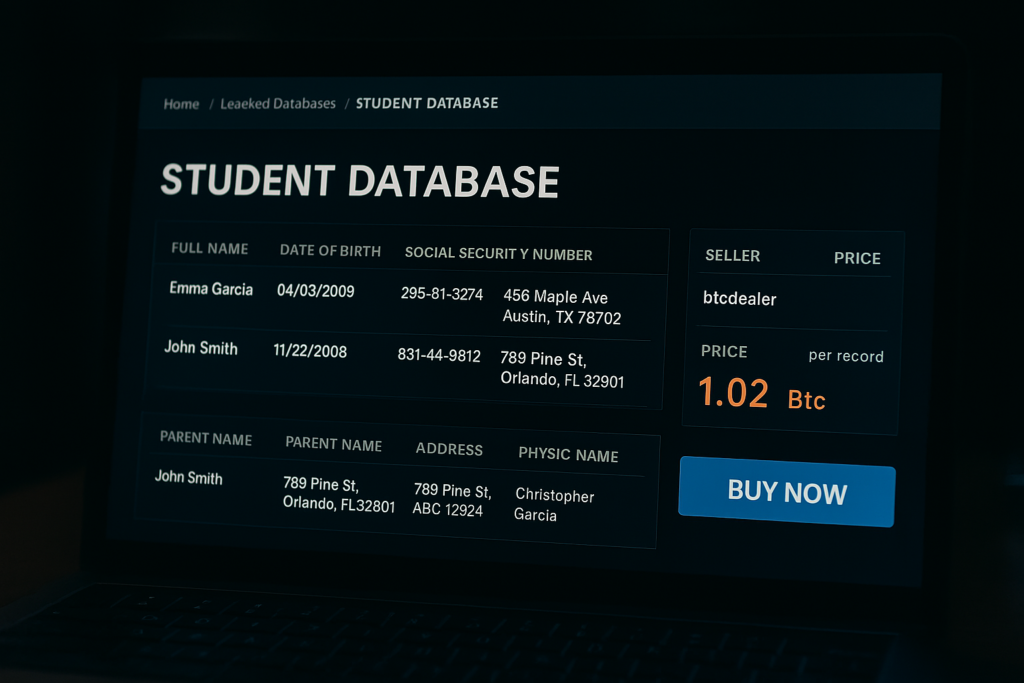
The risks of poor school cybersecurity go far beyond technical disruptions. We’re talking about life-altering consequences for students—and legal, financial, and reputational disasters for school systems.
🧬 1. Permanent Student Identity Theft
Student records contain a goldmine of sensitive data: full legal names, birthdates, Social Security numbers, addresses, parent/guardian contacts, and sometimes medical or disciplinary histories. Unlike adults, children’s credit isn’t monitored—making their data ideal for long-term fraud.
- A 2022 report by Javelin Strategy & Research found that 1 in 50 children was a victim of identity fraud that year—often without detection for 5+ years.
- Stolen data is often sold on dark web marketplaces for as little as $2 per student.
- Impacts include credit damage, denied student loans, IRS fraud alerts, and compromised immigration or health records.
“Freezing your child’s credit is one of the most robust protections you can take as a parent”
— Eva Velasquez, CEO, Identity Theft Resource Center
🧑🏫 2. Learning Disruptions
When a school network is compromised, it’s not just about losing access to Wi-Fi. It’s about losing access to education itself:
- Attendance systems fail, preventing schools from reporting funding-eligible student counts.
- Testing platforms crash, delaying critical assessments or invalidating scores.
- Special education tools like individualized education program (IEP) software may become inaccessible, violating legal obligations.
📊 According to K12 SIX, ransomware was the most frequently disclosed type of cyber incident in U.S. K–12 schools in 2021, with disruptions lasting days or even weeks, and some districts shutting down entirely.
For students already behind due to the pandemic, these delays can be devastating—especially for low-income or special needs students.
🔓 3. Physical Safety Concerns
Modern school infrastructures increasingly rely on digital integration for various physical security systems, including security cameras, badge access controls, fire alarms, and intercom systems, often managed via Wi-Fi or cloud-based platforms. While this integration enhances operational efficiency, it also introduces vulnerabilities that can be exploited through cyberattacks.
Potential Risks:
- Unauthorized Access to Security Systems: Cyber intrusions can compromise surveillance systems, granting unauthorized individuals access to live camera feeds or recorded footage. For instance, vulnerabilities in IP surveillance systems can be exploited if proper cybersecurity measures are not in place.
- Compromise of Access Control Systems: Weaknesses in access control mechanisms can allow unauthorized individuals onto school premises, posing safety risks to students and staff. Ensuring robust security protocols is essential to prevent such breaches.
- Disruption of Emergency Communication Systems: Cyberattacks targeting intercom or alarm systems can disrupt emergency communications, hindering the school’s ability to respond effectively to incidents.
In March 2021, hackers gained unauthorized access to Verkada Inc.’s systems, compromising live surveillance footage from approximately 150,000 cameras across various organizations, including schools. This breach exposed sensitive areas within educational institutions, raising significant concerns about student and staff privacy.
The nightmare scenario isn’t just digital—it’s real-world harm made possible by digital vulnerability.
Recommendations:
To mitigate these risks, schools should consider the following measures:
- Conduct Regular Security Assessments: Evaluate both physical and cyber vulnerabilities within the school’s infrastructure to identify and address potential weaknesses.
- Implement Robust Access Controls: Ensure that access to critical systems is restricted to authorized personnel and that strong authentication methods are in place.
- Educate Staff and Students: Provide training on cybersecurity best practices to reduce the risk of phishing attacks and other common threats.
- Develop Incident Response Plans: Establish and regularly update protocols for responding to cyber incidents to minimize potential impacts on physical security systems.
By proactively addressing these vulnerabilities, educational institutions can better protect their integrated systems from cyber threats, thereby ensuring the safety and security of their students and staff.
🛠 What Schools Can Do—Even Without a Big Budget

Even the most underfunded districts can raise their cybersecurity baseline. The goal isn’t perfection—it’s resilience. Even small steps toward stronger school cybersecurity systems—like basic access control, phishing training, and software updates—can make a huge difference in preventing a student data breach.
🔐 Basic Protections (Minimum Required)
- Multi-Factor Authentication (MFA): Essential for admin panels, teacher logins, and any financial or HR system.
- Automatic Patching: Keep operating systems and critical software updated across all devices.
- Least-Privilege Access: Limit admin-level access to only essential users. Students should not have install or settings permissions.
These are low-cost, high-impact safeguards that can be implemented with existing tools.
🧑🏫 Train Staff & Students
Human error remains the #1 cause of breaches. Even a high schooler clicking on a phishing link can give attackers a foothold.
👉→ Explore actionable tips for building a culture of cyber hygiene.
- Run phishing simulations every semester for all staff and admin users.
- Provide age-appropriate digital literacy lessons on privacy, phishing, and password safety.
- Encourage a culture of cyber accountability—where reporting suspicious activity is normalized, not punished.
🧰 Use Free & Subsidized Tools
Many top-tier tools offer free or heavily discounted licenses to K–12 institutions:
- Google Admin Console – Use centralized control to enforce login security, block risky extensions, and disable open device access.
- Cisco Umbrella for Schools – Free DNS-level protection from malware and phishing domains.
- Cloudflare for Education – DNS and DDoS protection at no cost for verified schools.
- K12 SIX (K–12 Security Information eXchange) –Cyber threat intelligence, real-time alerts, and best practices curated for school districts.
- Microsoft Defender for Endpoint (Education) – Includes malware protection, threat analytics, and policy enforcement.
💡 Bonus Tip: Contact local colleges or cybersecurity nonprofits. Many offer free training, network audits, or student-led cybersecurity assistance programs for public schools.
🏛 Policy Solutions: How Government Can Help
Until recently, cybersecurity policy for schools was slowly gaining momentum. CISA, the FBI, and the Department of Education had begun coordinating to share threat data, build training resources, and recommend low-cost cybersecurity best practices.
But in 2025, that progress stopped cold.
The Trump administration’s sweeping cuts to CISA and its executive order to dismantle the Department of Education have left school cybersecurity efforts stranded. The very agencies that were beginning to coordinate national support have now been defunded, dismantled, or disbanded entirely.
What We’ve Lost:
- CISA’s K–12 Cybersecurity Advisory Committee has been disbanded.
- Federal coordination between the Department of Education, FBI, and NSC has ceased.
- No new cybersecurity funding has been allocated to replace expired COVID-era relief.
“President Trump and Elon Musk’s reckless approach to dismantling agencies like the Department of Education and CISA is undermining our ability to protect our schools and communities from cyber threats.”
— Rep. Doris Matsui (D-CA)
What States Can Still Do:
In the absence of federal leadership, the burden now falls on state governments, school boards, and local coalitions to close the cybersecurity gap. Here’s where energy must shift:
✅ Create or Expand State-Level Cyber Grants
States like New York and Texas have pioneered initiatives to bolster school cybersecurity:
- New York’s Smart Schools Bond Act: Approved by voters in 2014, this act authorized the issuance of $2 billion in bonds to finance educational technology and infrastructure improvements aimed at enhancing learning opportunities statewide.
- Texas’ Cybersecurity Funding: In 2023, the Texas Legislature allocated $55 million to the Texas Education Agency to combat the rising incidents of ransomware and other cyber threats targeting school districts across the state.
✅ Mandate Minimum Cybersecurity Standards at the State Level
Establishing baseline digital safety regulations is crucial. Just as fire codes ensure physical safety, standardized cybersecurity protocols can protect student records, communication systems, and physical infrastructure from digital threats. Implementing these standards ensures a uniform level of protection across all educational institutions within the state.
✅ Partner with Higher Ed and Private Sector Volunteers
Collaborations with local colleges, universities, and private sector organizations can provide schools with valuable resources:
- Google’s Cybersecurity Clinics: In 2023, Google awarded over two dozen colleges and universities $1 million each to establish cybersecurity clinics. These clinics aim to expand access to cybersecurity education and can serve as a resource for local schools seeking expertise and assistance.
- Texas Tech University’s Initiative: Texas Tech, in partnership with other universities, received a $2.5 million grant from the U.S. Department of Defense to develop a comprehensive cybersecurity research and workforce development program. Such programs can be instrumental in providing training and resources to local schools.
✅ Protect What’s Left of E-Rate
The Federal Communications Commission’s (FCC) E-Rate program has been instrumental in providing schools with affordable broadband access. Recognizing the evolving cyber threat landscape, the FCC initiated a three-year, $200 million Cybersecurity Pilot Program in 2023 to study the effectiveness of using universal service funds for cybersecurity services and equipment in schools and libraries. States should advocate for the expansion of such programs to explicitly cover firewalls, endpoint security, and cybersecurity staffing, ensuring that schools have the necessary resources to protect against cyber threats.
By focusing on these areas, state and local entities can play a pivotal role in safeguarding our educational institutions against the growing tide of cyber threats.
📢 Conclusion: School Cybersecurity Is Infrastructure. Treat It That Way.
America’s schools are under attack—not by armed intruders, but by silent, relentless cybercriminals. The most vulnerable institutions are being targeted: schools with old systems, no cybersecurity staff, and no backup plan.
The damage is real: stolen identities, canceled classes, leaked psychological reports, and compromised physical safety systems.
And just as the threat grows, the federal response is being dismantled.
CISA’s funding has been gutted. The Department of Education is being torn down. Coordination between agencies has vanished.
This isn’t just bad policy—it’s an invitation to disaster.
School cybersecurity must be treated as essential infrastructure. When ransomware shuts down classrooms or exposes thousands of student records, it’s not a glitch—it’s a failure to protect children.
But if Washington won’t act, someone must.
States, school boards, local leaders, and tech partners still have options. There are free tools, affordable safeguards, and proven strategies that can make schools harder targets—even on limited budgets.
Cyberattacks are accelerating. Budgets are shrinking. Students are at risk.
The worst response now would be silence.
The next ransomware attack is already in motion—and our kids are still logged in.
If the federal government steps back, we have to step up.
🔥 Stay One Step Ahead of the Hackers. Get the latest AI-driven cyber threats and defense strategies delivered straight to your inbox. No spam, just smart insights. Sign up for our cybersecurity newsletter and updates here.
✅ Key Takeaways
- School cybersecurity is essential infrastructure—as critical as secure doors and clean water. It protects student privacy, learning continuity, and physical safety.
- Federal support is vanishing. With the dismantling of the Department of Education and deep cuts to CISA, schools are losing their last lines of centralized cybersecurity support.
- Threats are escalating. Ransomware attacks on K–12 schools rose 92% in a single year. Hackers are faster, smarter, and using AI-enhanced tools to target schools with minimal defenses.
- Most schools are unprepared. Only 12% of districts have a full-time cybersecurity staffer. Many still run decade-old infrastructure and lack basic protections like MFA or endpoint security.
- Local and state leaders must now lead. Without federal guidance, states must create grant programs, set minimum standards, and leverage local partnerships to protect schools.
- Cyberattacks are not just digital. They’re disrupting real classrooms, leaking sensitive student data, and even compromising physical security systems like door locks and surveillance feeds.
🧾 Frequently Asked Questions (FAQ)
Q: What is the biggest cybersecurity risk in schools?
A: Human error—especially phishing—is still the most common entry point. One mis-clicked link can give attackers full access to a school’s network.
Q: Can students’ identities really be stolen through a school hack?
A: Yes. School records often contain full legal names, Social Security numbers, and medical or disciplinary data. Kids are prime targets because their credit isn’t monitored for years.
Q: Why aren’t schools better protected?
A: Budget cuts, outdated infrastructure, and lack of trained staff. Federal programs like E-Rate don’t cover cybersecurity tools, and recent political changes have eliminated agencies that were just starting to help.
Q: Has the federal government offered new help in 2025?
A: No. The Trump administration has dismantled the Department of Education and cut CISA’s funding, halting all coordinated cybersecurity efforts for schools at the federal level.
Q: What can parents do to help?
A: Support school bond measures, push for state-level cybersecurity funding, and teach kids good digital hygiene—like recognizing phishing attempts and using strong passwords.
