
The modern home is smarter than ever. Voice assistants respond instantly, thermostats adjust automatically, and even your refrigerator can detect when you’re out of oat milk. But beneath this convenience lies a massive vulnerability. In 2025, smart home devices are not just a luxury or a novelty, they’re a digital weak point waiting to be exploited.
As billions of IoT devices flood homes globally, a consistent pattern is emerging: smart home tech remains far behind in smart home cybersecurity standards. Whether it’s a $10 smart plug or a high-end surveillance system, these connected devices often lack even the most basic protections against smart device vulnerabilities. And that matters because if just one device is compromised, your entire home network could be at risk.
This blog dives into why smart home devices remain the most exploitable entry point for cyberattacks, how AI is changing the game, and what we can do about it as users, manufacturers, and policymakers, to reduce smart home cybersecurity weaknesses and connected home risks.
The Smart Home Security Paradox: Convenience vs. Risk
Why Adoption Outpaces Security
The global smart home security market is growing fast: from $28.4 billion in 2023 to an expected $107.1 billion by 2033, (Scoop Market Research). But this rapid growth outpaces the implementation of proper security measures. Startups and original equipment manufacturers (OEMs) race to meet demand, prioritizing features, integrations, and ease-of-use over robust cybersecurity in smart homes.
Surface Area Explosion

The number of connected IoT devices is projected to reach 18.8 billion by the end of 2024, a 13% year-over-year increase. Every new device adds a new attack vector, expanding the smart home cybersecurity weakness. Even seemingly harmless gadgets like smart bulbs and digital assistants can be exploited as entry points into your network.
Lack of Visibility and Control
Most users don’t understand what data their smart home devices collect or where it’s being sent. Default settings often favor usability over privacy, leaving users with little control over permissions, data sharing, or firmware access; key contributors to IoT security risks.
Real-World Breaches: How Smart Devices Were Compromised
The Mirai Botnet (2016) and Its Legacy
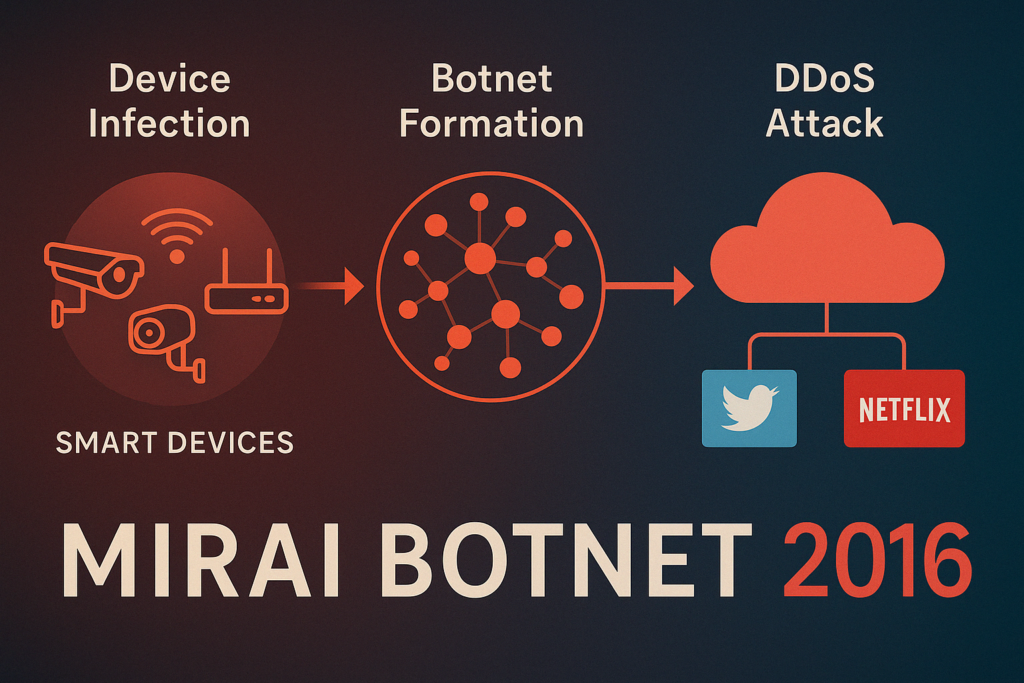
The Mirai malware exploited IoT devices using default usernames and passwords, forming a botnet that launched a massive DDoS attack on Dyn in 2016. This attack disrupted access to Twitter, Netflix, and many other major websites.
Unfortunately, many devices remain vulnerable to similar exploits due to unchanged credentials and unpatched firmware, highlighting persistent smart device vulnerabilities.
Smart Locks and Alarms: False Sense of Security
In a 2022 study, researchers discovered vulnerabilities in Sceiner smart locks that allowed remote unlocking via firmware manipulation.
Other smart security systems have been jammed or bypassed using radio interference and over-the-air (OTA) exploit techniques, serious cyber threats in smart homes.
Baby Monitors, TVs, and Voice Assistants as Listening Devices
A 2016 study found that Samsung’s SmartThings platform had critical vulnerabilities that could allow hackers to remotely trigger fire alarms or unlock doors.
With devices like Alexa and Google Home constantly listening for commands, attackers have used techniques like ultrasonic sound or deepfake audio to manipulate smart assistants, adding to the growing list of smart home cybersecurity concerns.
Supply Chain Vulnerabilities in OEM Components
Many manufacturers use common software libraries or chipsets sourced from third parties. If just one of these upstream components is vulnerable, it can impact thousands of devices from different brands.
Why Smart Home Devices Lag Behind Other Tech in Cybersecurity
Fragmented Ecosystem and Lack of Standards
IoT device security remains inconsistent. While NIST has released frameworks like SP 800-213, there is no universally adopted set of standards. Many consumer-grade products are never designed to meet enterprise-level security expectations, adding to widespread connected home risks.
Cost-Driven Design Philosophy
With thin margins and rapid development cycles, many smart devices are released with minimal security protections. Manufacturers often rely on “security through obscurity” rather than investing in actual defenses, exacerbating the smart home cybersecurity weakness.
Update and Patchability Challenges
Many devices lack over-the-air (OTA) update functionality. If a vulnerability is discovered, there may be no way to fix it without replacing the device entirely. This results in long-term smart device vulnerabilities, especially as AI-powered threats evolve faster than legacy hardware can keep up. Learn more about how outdated systems are actively being exploited by AI-enhanced threats in our breakdown: The AI-Powered Malware Time Bomb.
User Neglect and Misconfiguration
Users often don’t change default credentials, segment their home networks, or enable available security features. Even when best practices are known, configuration complexity can be a barrier, exposing users to unnecessary IoT security risks.
The AI Acceleration Effect: Smarter Attacks, Dumber Defenses
AI-Driven Reconnaissance on Home Networks
AI can be used by attackers to automatically scan networks, identify outdated firmware, and prioritize the most vulnerable targets, posing a new wave of cyber threats in smart homes. These automated scans are just one tactic in a growing arsenal of AI-enabled attacks. For a deeper dive into proactive defenses, check out 7 AI Cybersecurity Best Practices.
Deepfake Voice Commands and Smart Assistant Hijacking

Attackers are now generating synthetic voices that mimic household members. In some documented cases, they’ve tricked smart assistants into executing unauthorized actions, expanding the landscape of smart home cybersecurity threats.
Machine Learning Exploits in Smart Cameras and Sensors
By feeding misleading data to camera models or AI-based motion sensors, attackers can cause them to ignore intrusions or mislabel threats, another form of smart home cybersecurity weakness.
Defensive Measures: What Users, Vendors, and Governments Can Do
At the Individual Level
Users should:
- Separate IoT and personal devices using network segmentation
- Regularly update passwords and device firmware
- Disable unnecessary features and remote access points
We cover smart home cybersecurity threats like this in our newsletter, subscribe here to stay informed and protected.
At the Manufacturer Level
Device manufacturers should implement:
- Secure-by-design principles and hardware-backed encryption
- Support lifecycles with guaranteed OTA updates
- Vulnerability disclosure programs
At the Government & Policy Level
Agencies like NIST have led the way with labeling efforts and router security benchmarks.
Governments should:
- Require minimum cybersecurity features in consumer-grade devices
- Penalize manufacturers that fail to patch known vulnerabilities
- Fund education and outreach on IoT security risks
Role of Zero Trust in the Home Environment
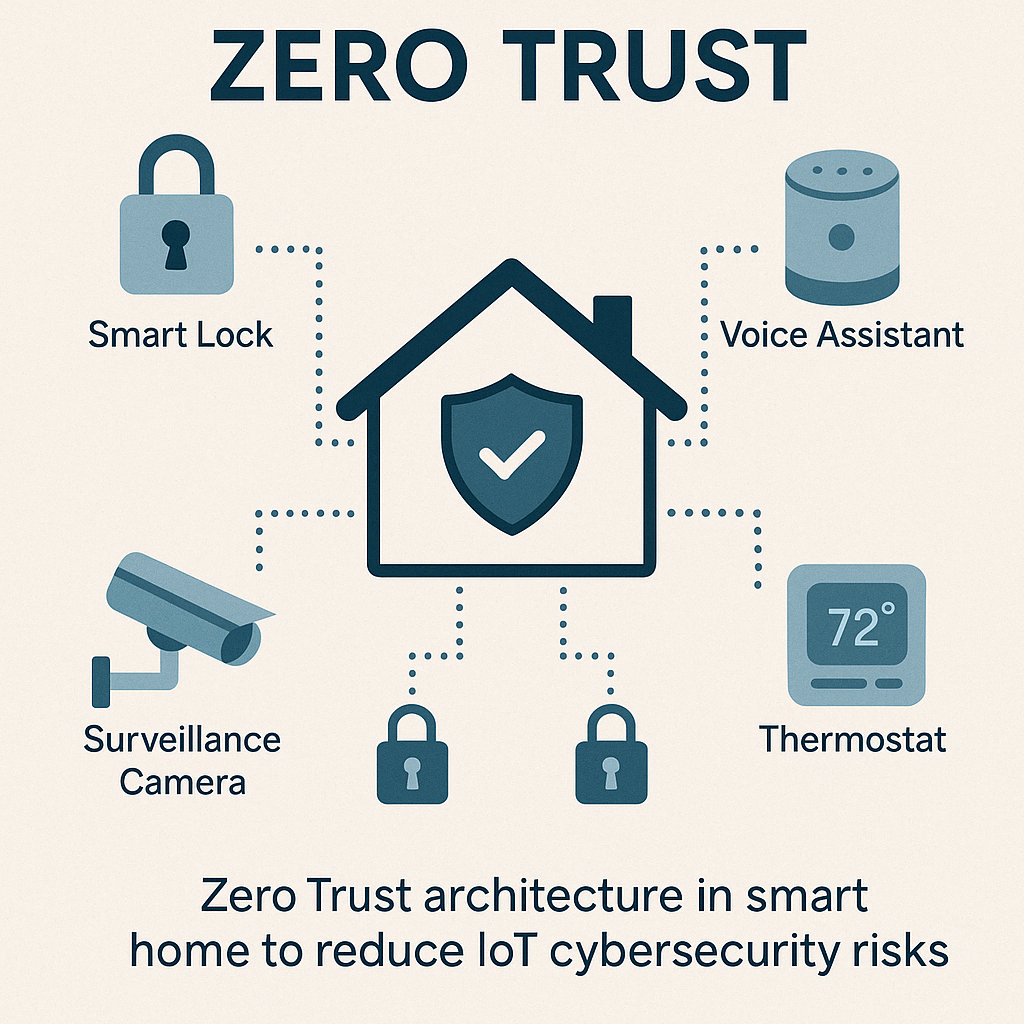
Zero trust isn’t just for enterprise. In a smart home, it means:
- Treating every device as potentially compromised
- Requiring authentication and encryption for all internal communications
- Enforcing least-privilege access
The Broader Implications: National Security, Privacy, and Surveillance
Smart Homes as National Security Soft Targets
Smart home devices near diplomats or government staff can be leveraged for surveillance or used in coordinated attacks. These risks have national security implications far beyond individual households.
Mass Surveillance by Accident (or Design)

From always-on microphones to unencrypted traffic, many devices are essentially always watching. In large ecosystems (Google, Amazon), this adds up to a mass surveillance apparatus.
Insurance, Liability, and Legal Gaps
Who pays when your hacked baby monitor leaks sensitive data? Legal clarity is lacking. Insurance companies are still working to define liability policies for smart home-related cyber incidents.
Conclusion & Future Outlook
Smart home cybersecurity remains one of the weakest links in modern digital infrastructure. The industry’s fragmented landscape, economic incentives, and regulatory gaps have all contributed to a situation where even tech-savvy users are at risk.
But change is coming. Expect AI-enhanced defense platforms, mandatory security certifications, and regulatory frameworks that push for longer update lifecycles and greater transparency.
To get weekly breakdowns like this with actionable insight and real-world threat analysis, sign up for our newsletter.
- For users: Audit your smart home devices today. Segment your network and disable anything you don’t need.
- For vendors: Build secure-by-design. Patching after the fact isn’t good enough.
- For policymakers: Standardize requirements before another breach reaches national scale.
For more on how AI is driving these changes, check out our blogs on:
The landscape is changing, and AI is at the center of both the threat and the solution. Explore the top innovations in AI-powered defense in Top AI Security Tools in 2025.
Want insights like this delivered weekly? Get expert analysis on AI-driven cyber threats, smart device vulnerabilities, and national security risks, sign up for our newsletter.
Key Takeaways
- Most smart home devices prioritize convenience over security
- Real-world breaches show how vulnerable these devices are
- The fragmented ecosystem lacks update support and security standards
- AI both magnifies threats and offers new defense options
- Users, vendors, and governments must all share responsibility
FAQ
Q1: What are the most vulnerable smart home devices today?
Devices like smart plugs, cameras, and bulbs that lack regular updates or authentication mechanisms.
Q2: Can smart home devices be hacked even if my Wi-Fi is secured?
Yes. Attacks can exploit default settings, open ports, or outdated firmware.
Q3: How do I secure my smart home network without being a tech expert?
Use a guest network for IoT devices, update passwords, and disable unnecessary features.
Q4: Are smart assistants like Alexa or Google Home safe to use?
They are better secured than most IoT devices, but they still pose risks, especially from voice spoofing.
Q5: Will AI make smart homes safer or more dangerous?
Both. It enables advanced attacks but also powers better detection and response tools.
