
Encrypted messaging plays a vital role in safeguarding private communication. But when government officials use these tools without proper oversight, the consequences can be serious. Signalgate—an accidental disclosure of classified military plans—revealed how encrypted messaging can contribute to national security failures when misused. This article unpacks what happened, why it matters, and what lessons we should take from it.
I. Introduction: The Illusion of Secure Messaging

In March 2025, a serious breach of national security occurred when U.S. officials accidentally added journalist Jeffrey Goldberg to a Signal group chat discussing classified military operations against the Houthis in Yemen. Dubbed “Signalgate,” the scandal revealed the dangers of using consumer-grade encrypted messaging apps like Signal for government business.
While end-to-end encryption (E2EE) has become the gold standard for digital privacy, it can also shield bad actors, obscure oversight, and complicate accountability. Signalgate underscores the double-edged nature of encrypted messaging: it protects legitimate privacy while enabling unauthorized secrecy. The incident triggered bipartisan scrutiny and a broader reevaluation of what privacy means in the context of national security.
II. What is “Signalgate”? Breaking Down the Event
Timeline of the Incident
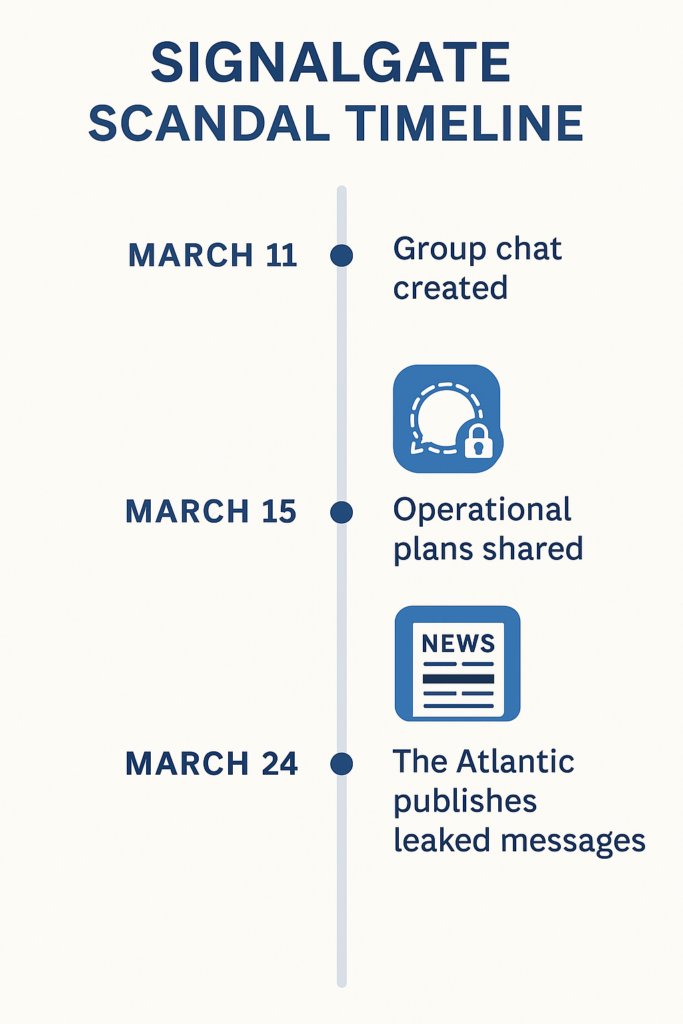
The timeline of Signalgate reflects a rapid unraveling of operational secrecy. On March 11, 2025, a Signal group chat was created by high-level national security officials. Just four days later, on March 15, Defense Secretary Pete Hegseth shared sensitive operational plans in that chat. Then, on March 24, journalist Jeffrey Goldberg—accidentally included in the group—published excerpts from the conversation in The Atlantic, revealing the extent of the breach and igniting national controversy. (The Atlantic).
Key Actors Involved
Key figures in the scandal included Vice President JD Vance, Defense Secretary Pete Hegseth, CIA Director John Ratcliffe, and National Security Advisor Mike Waltz. Their participation in the unauthorized Signal chat exposed a dangerous casualness about information security at the highest levels of government.
What Made This a ‘Gate’?
The leak wasn’t just an embarrassing slip—it involved highly sensitive military strategies and the unintentional identification of a CIA operative. The decision to use a disappearing message app instead of secure, regulated communication channels compounded the severity, raising legal, ethical, and national security alarms.
Public and Government Response
The response was swift and far-reaching. Media outlets seized on the story. National security experts decried the recklessness of using unsecured tools. Lawmakers demanded answers, and the Pentagon’s inspector general launched an official investigation into Hegseth’s conduct. (New York Post).
💡 Want more real-world breakdowns like this? Subscribe to Quantum Cyber AI for weekly insights on cybersecurity, AI, and national security.
III. Encrypted Messaging: Boon for Privacy, Tool for Evasion
The Rise of Signal, Telegram, and WhatsApp in High-Stakes Communication
Encrypted messaging apps are not inherently problematic. Signal, Telegram, and WhatsApp all offer end-to-end encryption that protects users from surveillance and interception—making them popular among journalists, activists, and whistleblowers. But their use by government officials for sensitive or classified communication creates a dangerous blind spot for oversight and compliance. (POLITICO).
How End-to-End Encryption Works

E2EE ensures that only the sender and the recipient of a message can decrypt and read it. The content remains opaque to service providers, internet intermediaries, and even platform developers. While this guarantees personal privacy, it also means that if sensitive content is shared via these platforms, there is no way for oversight agencies to review the communication retroactively. (Matthew Green’s Blog).
What Metadata Still Reveals
Even if message content is encrypted, metadata—such as sender and recipient identities, message timestamps, and app usage patterns—can still be accessed and analyzed. This data can be used to establish communication links, reveal behavioral patterns, and identify sensitive relationships, even when the actual content remains hidden. (Matthew Green’s Blog).
Vanishing Messages, Vanishing Accountability

Features like disappearing messages, screenshot restrictions, and ephemeral logs make encrypted messaging apps convenient for secrecy. But in the public sector, these features directly conflict with laws governing transparency and recordkeeping. In the case of Signalgate, the use of disappearing messages may have violated the Federal Records Act, as there was no institutional record of the communications. (Washington Post).
IV. When Privacy Tools Clash with National Security

The Intelligence Community’s Dilemma
U.S. intelligence agencies have long warned about the misuse of encrypted platforms. While protecting civil liberties is a core value, unauthorized or undocumented use of these tools by government actors obstructs lawful surveillance and internal oversight. In the context of Signalgate, national security personnel bypassed traditional communication safeguards. (POLITICO).
Real-World Precedents
Encrypted platforms have a track record of misuse:
- Paris attacks (2015): Terrorists used Telegram to coordinate.
- Capitol Riots (2021): Protesters used Signal for real-time planning.
- Drug cartels: Continue to use WhatsApp and Telegram to evade law enforcement. These examples illustrate how even well-intentioned privacy tools can become conduits for dangerous activity when left unregulated.
🔐 Encrypted messaging isn’t new in crisis situations. Read our deep dive on AI-Powered Cyberattacks on Critical Infrastructure to see how bad actors exploit blind spots.
Foreign Espionage via Encrypted Platforms

There is growing concern that foreign adversaries may exploit encrypted platforms for covert operations inside the U.S. Without oversight or institutional monitoring, such tools could allow hostile actors to coordinate undetected—even inside government agencies. (Reddit).
Whistleblowing vs. Leaking Classified Material
While tools like Signal have empowered whistleblowers, they also enable reckless or intentional leaking of sensitive government data. The distinction between exposing corruption and compromising national security often hinges on context, and the law struggles to draw clear lines in an encrypted environment.
V. Policy and Legal Ramifications
The Case for Regulating Encrypted Messaging
Legislative efforts like the EARN IT Act aim to make tech platforms more accountable for illegal activity enabled by their services. While encryption advocates argue this would weaken security, regulators contend that there must be mechanisms to ensure criminal behavior doesn’t hide behind impenetrable encryption.
Constitutional & Civil Liberties Concerns
Privacy organizations like the EFF and ACLU strongly oppose “backdoor” encryption mandates, warning they could undermine not just user privacy but also freedom of speech and association. They argue that once a vulnerability exists, it can be exploited not only by governments but also by hackers and authoritarian regimes.
Federal Records & Transparency Requirements
Under the Federal Records Act, all communications related to official business must be documented and preserved. Encrypted messaging apps, especially those with disappearing messages, inherently challenge this requirement. Signalgate presents a textbook case of noncompliance—where official communication left no audit trail. (Washington Post).
🧠 For another example of data oversight gaps, see our post on School Cybersecurity Under Attack in 2025.
Current & Proposed Legislation
Ongoing debates in Congress and international bodies reflect the complexity of regulating encryption. The EU has proposed lawful access mechanisms, and U.S. lawmakers continue to float encryption-curbing bills. But political and public resistance remains strong, especially in tech-literate constituencies.
VI. AI’s Role in Breaking (or Strengthening) Encryption
AI-Powered Metadata Analysis & Pattern Detection

AI is increasingly used to make sense of metadata—mapping communication flows, predicting affiliations, and inferring hidden connections. Even if content is encrypted, AI can draw valuable insights from behavior, usage frequency, and digital footprints. (Digital Watch Observatory).
🚨 Want to know how AI is being weaponized against secure systems? Check out 3-Second Hacking: AI Brute Force Attacks for the next phase of predictive threats.
Generative AI as a Disinformation Tool on Encrypted Channels
AI doesn’t just analyze—it creates. Disinformation campaigns using deepfakes or fabricated chat screenshots can be circulated within encrypted networks. This weaponization of generative AI poses new challenges for verifying authenticity in closed systems.
Could AI Ever Crack End-to-End Encryption?
While current encryption algorithms are secure against traditional computation, AI combined with quantum computing could eventually pose a threat. Machine learning could also optimize brute-force attacks or uncover implementation flaws in cryptographic protocols.
AI + Privacy: Tools for Securing More Than Just Text
AI also enhances privacy technologies—securing voice, video, and biometric data. Advances in zero-knowledge proofs, homomorphic encryption, and privacy-preserving AI architectures are redefining what “end-to-end” can mean across multiple data types.
VII. Response Strategies: What Governments and Organizations Can Do
Internal Policy Audits & Device Management
Agencies must conduct audits to identify unauthorized encrypted app usage. Government devices should either block or tightly control installation and usage of messaging apps. Whitelisted apps should go through rigorous vetting processes.
Training for Digital Hygiene and Legal Compliance
All personnel handling sensitive information must receive cybersecurity training that covers legal obligations. This includes how to recognize inappropriate usage, comply with retention rules, and understand when encryption is—and isn’t—permissible.
Incident Response Protocols for Encrypted Messaging Abuse
Organizations need clear playbooks for responding to breaches or leaks involving encrypted apps. This includes technical forensics, legal containment, public relations, and accountability reviews. Preparedness can mitigate long-term damage.
Public Awareness and Media Literacy Campaigns
Beyond government, public education on the limits and responsibilities of encryption is vital. Campaigns should focus on the difference between security and secrecy, and encourage responsible use of privacy-enhancing technologies.
VIII. Conclusion: Privacy vs. National Security in a Post-Signalgate World
The Signalgate scandal illustrates what happens when powerful privacy tools are misused by those entrusted with national defense. It’s a wake-up call that encryption, without accountability, becomes a liability—not just a protection.
Rather than framing privacy and national security as enemies, we must innovate systems that accommodate both. That means building encryption standards that support lawful oversight, training leaders in responsible tech use, and enacting smart legislation that bridges the gap between security and civil rights.
Encryption is not the enemy—but misusing it might be.
📬Stay ahead of the next digital crisis. Join our newsletter to get expert briefings from Quantum Cyber AI.
IX. Key Takeaways
- Encrypted apps like Signal can create significant national security risks when misused.
- Signalgate exposed classified government communications via an accidental leak.
- Disappearing messages and lack of oversight undermine transparency requirements.
- AI-powered tools are both a risk and a solution in the encryption debate.
- Agencies must adopt strong internal policies and employee training.
X. FAQ Section
Q1: Can end-to-end encrypted messages ever be recovered by law enforcement?
No. Unless the device is compromised or a backdoor exists, E2EE prevents third parties—including law enforcement—from accessing message content.
Q2: Isn’t using Signal legal for government officials?
Yes, but only under strict guidelines. Using Signal for classified communication without proper controls may violate federal laws.
Q3: What’s the difference between privacy and secrecy in encrypted apps?
Privacy protects legal and ethical personal or professional data; secrecy involves concealment of information that may require lawful oversight.
Q4: Could future technology make encryption obsolete or irrelevant?
Possibly. Quantum computing and AI may eventually compromise current encryption, but post-quantum cryptography is already in development.
Q5: How can an organization responsibly use encrypted messaging tools?
By setting clear policies, restricting usage to approved apps, preserving logs where needed, and training staff on legal implications.
