
In March 2025, U.S. Defense Secretary Pete Hegseth mistakenly added journalist Jeffrey Goldberg to a Signal group chat intended for high-level discussions about military operations in Yemen. The revelations that followed were explosive: not only had classified details been shared over a consumer encrypted messaging app, but this wasn’t even the only group Hegseth was managing. A second Signal group included his wife and personal lawyer. The event quickly earned its moniker: the Signalgate scandal.
What appeared at first to be a routine lapse in digital hygiene turned into a flashpoint that exposed systemic vulnerabilities in how sensitive communications are handled at the highest levels of government. Investigations from the Pentagon Inspector General, CIA, and NSA followed, sparking widespread debates about the use of encrypted apps, operational security, and compliance with public records laws. But beyond the halls of government, something else happened: downloads of secure messaging apps exploded.
📝 Missed the full breakdown of the original Signalgate leak?
Read our earlier post: Encrypted Messaging Crisis: 5 Critical Lessons from Signalgate for the timeline, key figures, and national security fallout.
This follow-up takes a deep dive into how the Signalgate scandal became a catalyst for change. From surging adoption of secure messaging apps to the murky legal frameworks that surround them, we’ll examine the risks, opportunities, and lessons every organization should heed.
What Is Signalgate? A Quick Recap of the Scandal
The Accidental Leak That Sparked Global Headlines

The scandal began with a simple but consequential mistake: adding the wrong participant to a group chat. When Defense Secretary Pete Hegseth accidentally included journalist Jeffrey Goldberg in a Signal thread involving military strike discussions, the implications were immediate and global. According to The Guardian, the chat contained information about classified operations in Yemen.
A Second Signal Chat Made Things Worse
Just weeks later, another revelation added fuel to the fire. A second Signal group chat, this one reportedly created by Hegseth himself, included unauthorized recipients such as his wife and personal lawyer. The misuse of secure messaging apps at such a high level triggered questions about internal controls, information governance, and national security.
Fallout and Investigations
The fallout was swift. The Pentagon Inspector General opened a formal investigation. Additional audits were launched by the CIA and NSA to assess internal communication protocols and identify other possible breaches.
Why Secure Messaging Apps Are Suddenly Booming
Surging Demand in the Wake of Government Breaches
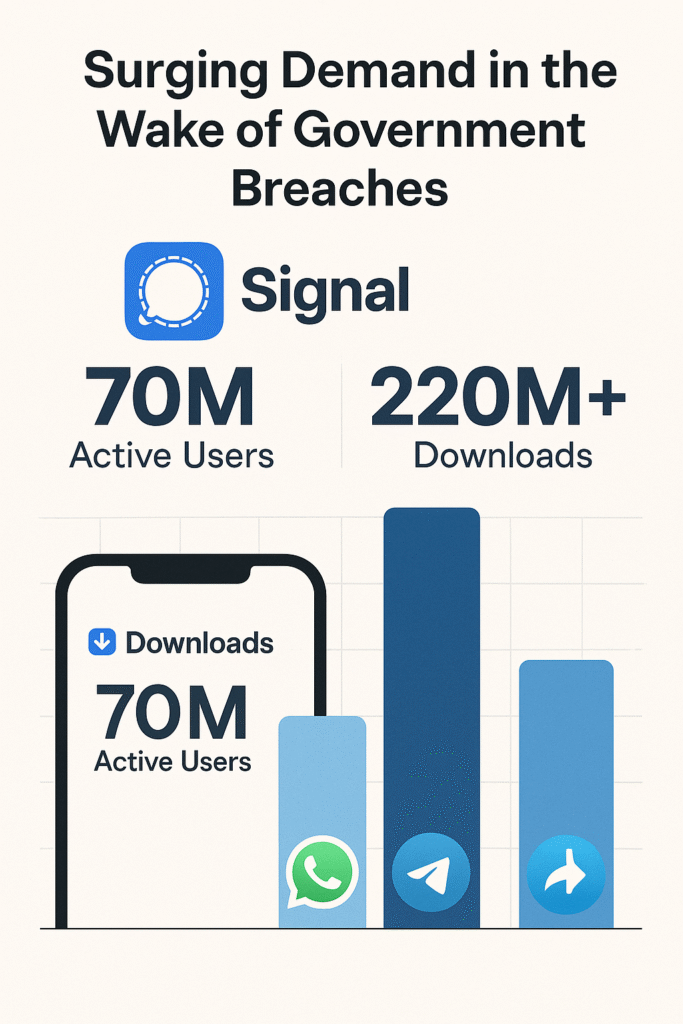
The public reaction was immediate and measurable. In the days following the Signalgate revelations, Signal experienced a significant uptick in downloads. According to Appfigures, downloads rose by 26% on the day the news broke, reaching 193,000 the next day and 195,000 the day after, nearly doubling its average daily downloads of 95,000. This surge marked the most substantial growth period in Signal’s history, highlighting a cultural shift toward privacy-first digital communication.
Broader Trends Driving Adoption
The rise of secure messaging apps isn’t limited to one incident. Messaging platforms globally now serve over 3 billion users, with WhatsApp leading the pack at 2 billion monthly active users. As headlines increasingly highlight surveillance, cyber espionage, and hacks, both consumers and institutions are shifting toward tools that prioritize encrypted communication.
Privacy-First Culture Gains Ground
Data breaches, whistleblower exposure, and global unrest are redefining what digital security means. From journalists in repressive regimes to executives managing M&A deals, the push for secure messaging apps reflects broader encrypted messaging trends.
A relevant case: In 2025, multiple organizations cited rising tensions in the Middle East and North Africa as a reason for accelerating the adoption of secure platforms to replace traditional email systems.
Institutional and Enterprise Uptake
Beyond the general public, secure apps are being integrated into the workflows of NGOs, corporations, and even healthcare providers. Yet, many organizations are still unclear on how to govern these tools. This lack of clear internal policy introduces new risks, even as adoption grows.
One urgent question remains: are institutions fully prepared to handle the legal and operational complexities that come with these tools?
This growing concern mirrors the urgency we covered in “Shocking Rise in AI Voice-Cloning Scams: 5 Cybersecurity Threats You Must Know.“
The Legal Grey Zone: Encrypted Messaging vs. Compliance
Government Use Without Oversight
Encrypted apps promise security but can conflict with transparency obligations. An Associated Press investigation in 2025 revealed that over 1,100 U.S. government officials were using Signal or WhatsApp with no effective archiving system in place. This isn’t just a federal problem. In 2023, Florida’s Governor’s Office faced scrutiny after staff used encrypted apps for public business without retention protocols. Watchdog groups like CREW have warned that such practices erode public accountability and create legal exposure if audits or subpoenas arise.
FOIA and Sunshine Laws in the Dark
Encrypted communications often evade records requests under laws like FOIA. Because they are not logged or centrally stored, they fall outside traditional public recordkeeping systems. This loophole has been cited in recent legal cases, including disputes over communications within city councils and state agencies. The issue has sparked lawsuits in several states. In one 2022 California case, Signal messages between city councilmembers were ruled undiscoverable due to the app’s disappearing message feature. Transparency advocates argue that FOIA laws urgently need modernization to address the proliferation of unlogged digital communications.
Private Sector Risk of Overreach
In contrast, some companies have responded with heavy-handed surveillance to mitigate compliance risk, a tactic that can backfire. According to attorney Aaron Hall, excessive monitoring can violate employee rights and trigger legal action. A 2023 Gartner survey found that 61% of employees believed they were being excessively monitored, which correlated with lower job satisfaction and retention. The rise of encrypted apps has intensified this tension, with some firms banning them entirely, only to face backlash over productivity and trust.
Lack of Unified Regulation
The legal risks of encryption are amplified by the fact that there is no unified federal guidance on how encrypted messaging should be governed. This regulatory gap leaves institutions to patch together ad hoc policies, which often lack rigor and consistency. Industry-specific laws like HIPAA, SOX, and GDPR offer partial guidance, but none address encrypted messaging directly. The SEC fined multiple financial institutions in 2022–2023 for failing to retain WhatsApp and iMessage business communications, highlighting the enforcement gap that encrypted apps now exploit.
Security Isn’t Just Privacy: Operational Risks of Over-Reliance
Encryption ≠ Immunity
It’s easy to confuse end-to-end encryption with bulletproof security. While encrypted messaging apps like Signal excel at protecting messages in transit, they do nothing to prevent user-side mishandling, as Signalgate made abundantly clear. Signal’s own support documentation emphasizes that while its cryptography is secure, it can’t protect against endpoint compromise or human error. In high-risk environments, encryption must be paired with strict operational protocols, not just secure apps.
Insider Threats Are Rising
Insider threats remain one of the most overlooked vulnerabilities. According to SentinelOne and Nisos, insiders account for nearly 60% of all data breaches. Verizon’s 2024 Data Breach Investigations Report confirms that insider misuse, particularly involving unmonitored tools, remains one of the top three causes of data loss. These aren’t always malicious actors; many are unaware they’re violating policy.
When users gain access to encrypted channels without proper controls, the illusion of security can lead to catastrophe. This mirrors the concerns explored in our post on “AI-Powered Malware Time Bomb: 5 Shocking Cyber Threats & How to Stop Them.“
Overconfidence in Messaging Tools
Secure messaging apps are often rolled out with minimal training, creating a false sense of invulnerability. This overconfidence can lead to lax policy enforcement, inconsistent usage, and risky behavior. Tools like Slack and Teams, while also vulnerable, offer administrative controls and audit trails. Encrypted apps like Signal often lack even basic user provisioning or message logging, leaving organizations blind to misuse.
Logging and Audit Blind Spots
Most secure messaging apps do not maintain detailed logs or metadata. While this supports privacy, it complicates incident response and compliance auditing. In cases of misuse, the lack of logs makes retrospective investigation nearly impossible. Without metadata or forensic access, incident response teams often hit dead ends. In regulated industries, this makes Signal and similar tools noncompliant by default unless paired with external logging infrastructure, which most organizations don’t implement.
Winners of the Encryption Arms Race: Signal, Session, and More
Signal’s Strengths and Weaknesses
Signal is open-source and offers true end-to-end encryption with minimal metadata collection. However, it lacks enterprise-grade features such as message archiving, administrative controls, or integrations with compliance tools, limitations that matter in regulated environments.
Session’s Metadata-Free Model
Session stands out by eliminating metadata altogether. Using a decentralized, onion-routed network and no phone number requirement, it excels in anonymity. But this design makes it difficult to manage in enterprise settings.
Telegram, Threema, Wickr – Varying Models
Telegram offers end-to-end encryption only through optional “Secret Chats.” Threema allows anonymous use and stores no contact data. Wickr, meanwhile, is often favored by businesses for its self-destructing messages and advanced compliance settings.
Choosing Based on Use Case
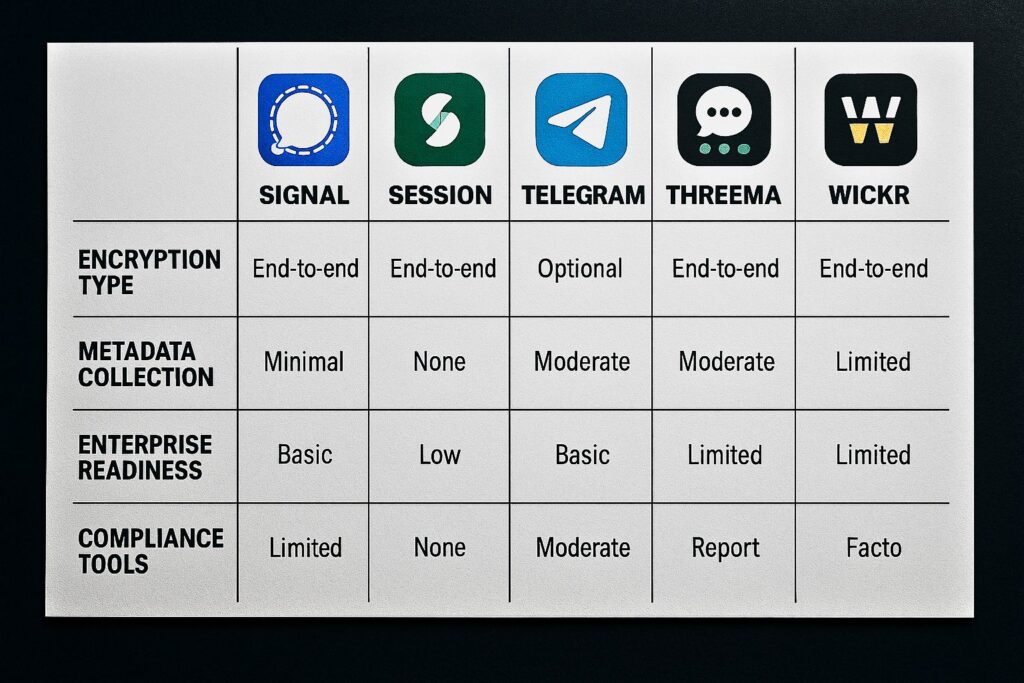
There is no one-size-fits-all solution. Each app offers trade-offs. Organizations must evaluate based on compliance requirements, operational needs, and threat models. For example, Wickr is favored by healthcare and defense organizations due to its compliance features, while Session is ideal for activists or whistleblowers who need anonymity. Threema offers a strong balance of privacy and usability for European users concerned with GDPR. The right tool depends on both your regulatory environment and your internal controls.
What Comes Next? Policy, Oversight, and the Future of Messaging
Regulatory Response Is Coming
In the wake of Signalgate, U.S. federal agencies are reexamining their messaging protocols. Analysts predict new regulations mandating encrypted communications to meet logging or auditability standards. Some policymakers have proposed “whitelisted apps” for government use, requiring vetting by federal IT or security agencies. CISA and the GSA have both issued internal memos urging agencies to reassess their encrypted messaging policies after Signalgate.
New Messaging Standards for Public Officials
Some state legislatures, including in California and New York, are exploring rules requiring encrypted messages to be logged and archived for public officials. The trend suggests a future in which public sector use of secure messaging apps will be subject to greater scrutiny.
Market Growth and Fragmentation
The global secure messaging market is expected to expand significantly, with region-specific apps gaining traction. However, fragmentation may introduce new interoperability and compliance challenges.
Many of these challenges overlap with themes from our post “AI Cyberattacks Are Exploding: Top AI Security Tools to Stop Deepfake Phishing & Reinforcement Learning Hacks in 2025.“
A Call for Balanced Innovation

Policymakers and developers alike must pursue encryption that preserves both privacy and accountability. This includes exploring new forms of “verifiable encryption” and platform-level auditability that respect user privacy while supporting institutional compliance. Researchers are exploring “verifiable encryption,” which allows message transmission to be cryptographically verified without revealing content. Other ideas include zero-knowledge proofs and policy-based key escrow, concepts designed to bridge the gap between privacy and institutional accountability.
Conclusion
Signalgate was more than a security lapse, it was a high-profile warning shot. When military communication leaks occur over apps built for privacy, not governance, the consequences aren’t just political, they’re operational, legal, and global.
Secure messaging apps have moved beyond niche adoption. They now occupy the center of conversations about privacy, policy, and power. But the tools we use must be matched by the systems we build around them. Encryption is not a substitute for judgment, policy, or oversight.
To get weekly breakdowns like this and explore how emerging tech is reshaping cybersecurity, subscribe to the Quantum Cyber AI newsletter. You’ll get deep dives, urgent alerts, and expert breakdowns delivered straight to your inbox.
✅ Key Takeaways
- The Signalgate scandal exposed how human error, not encryption itself, poses the greatest risk in secure communication.
- Secure messaging adoption is surging, driven by surveillance fears and operational privacy demands.
- Legal systems are lagging, leaving encrypted communications in a compliance grey zone.
- Insider threats and poor governance often undermine the benefits of secure messaging.
- No messaging app is universally ideal, fit depends on use case, compliance needs, and internal policy.
- Regulation is catching up fast; expect new standards in both public and private sectors.
❓ FAQ
Q1: Was Signal actually breached in the Signalgate scandal?
A1: No. Signal’s encryption was intact. The issue stemmed from user error, not a flaw in the platform.
Q2: Are encrypted messages subject to FOIA or public records laws?
A2: Typically not. Because these messages aren’t archived centrally, they often fall outside FOIA obligations unless retained separately.
Q3: Which secure messaging app is best for enterprise use?
A3: Wickr is often preferred due to compliance features like self-destructing messages, logging, and administrative controls.
Q4: What regulations exist for encrypted messaging in the U.S.?
A4: There is currently no unified federal law. However, state-level efforts and agency reviews are underway.
Q5: Can using apps like Signal or Telegram cause employment issues in sensitive roles?
A5: Yes, especially for government employees or executives subject to records laws or internal policies on communication tools.
