
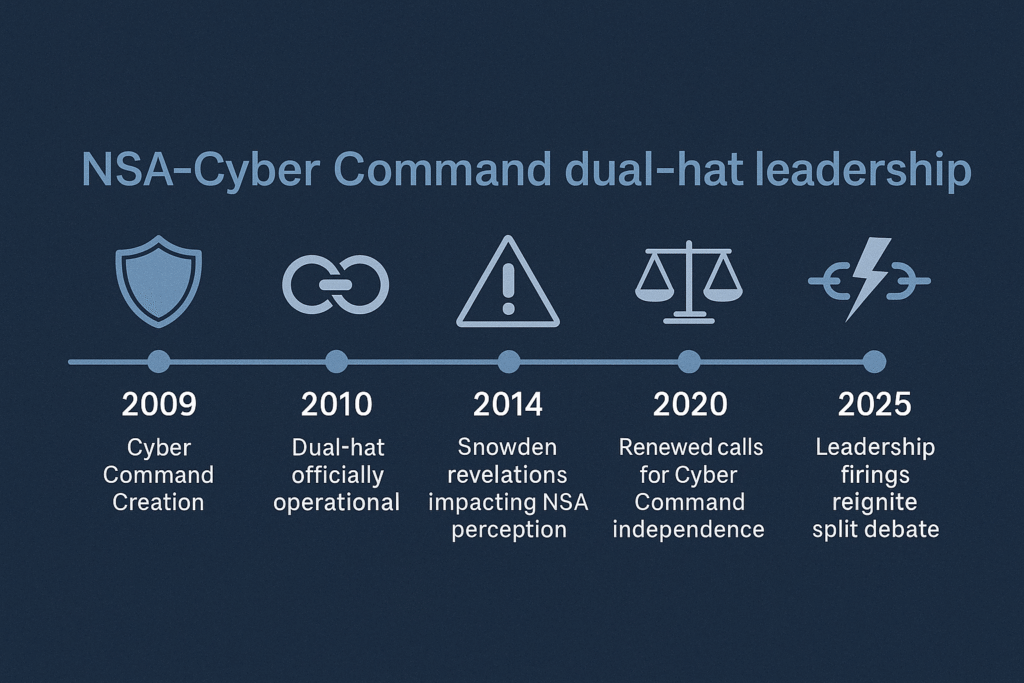
When seconds matter, coordination is everything, and splitting NSA and Cyber Command could shatter America’s fastest line of cyber defense. The debate around the NSA Cyber Command dual-hat leadership has moved from theoretical policy discussions to urgent national security questions. As recent leadership turmoil and rising cyber threats have shown, the way the U.S. organizes its cyber operations could determine whether we can fend off future attacks—or fall victim to devastating intelligence failures in 2025.
The NSA Cyber Command dual hat structure was designed for speed, cohesion, and overwhelming cyber force. Intelligence collection and offensive cyber operations were fused into a single operational vision, allowing the United States to launch rapid strikes against emerging threats without bureaucratic delays. This model proved critical during operations against ISIS, where seamless information flow enabled cyber disruptions within hours, not days (Cyber Command, NSA Successes Point Way to Future – Defense.gov).
Yet mounting political pressure has reignited arguments for a Cyber Command split. Policymakers cite concerns about oversight, transparency, and mission conflict between a civilian intelligence agency and a military command. These debates, once confined to closed-door hearings, have burst into the public arena—especially as cyber threats escalate dramatically. In 2021, the Colonial Pipeline ransomware attack demonstrated how swiftly a cyber event can cripple critical infrastructure. More recently, state-sponsored actors like China’s Volt Typhoon campaign have infiltrated U.S. energy grids and communications networks, operating stealthily across both military and civilian sectors (Ex-CISA boss says Trump actions risk ‘dangerously degrading’ US cyber defenses – Reuters).
Against this backdrop, dismantling the NSA Cyber Command relationship could introduce fatal delays, fractured intelligence pipelines, and weakened national readiness. In this post, we’ll break down exactly why dismantling this structure could backfire catastrophically, drawing from real-world examples, historic intelligence mistakes, and the strategic consequences the U.S. could soon face if the split occurs at the worst possible time.
Why the NSA and Cyber Command Relationship Matters

The Strategic Value of Unified Leadership
The dual-hat model—one leader overseeing both agencies—was created to align two critical missions: gathering intelligence and launching cyber operations. According to U.S. Cyber Command’s historical documentation, the structure ensures seamless coordination between data collection and military execution, removing bureaucratic delays at critical moments (Command History – Cybercom).
This unity has proven vital in real-world cyber conflict, where offensive and defensive lines blur and rapid information sharing is essential. In a cyber domain where attack windows can shrink to minutes, the ability to immediately translate surveillance insights into operational action often marks the difference between neutralizing a threat and suffering serious damage.
Moreover, dual-hat leadership provides a unified strategic vision. Instead of agencies competing over jurisdiction or priorities, the NSA and Cyber Command can pursue synchronized goals, whether disrupting terrorist networks, countering nation-state hackers, or defending critical infrastructure. As adversaries increasingly blend espionage, disinformation, and cyberattacks into single hybrid campaigns, this fusion of intelligence and operational authority is no longer a luxury, it is a necessity.
Examples of Rapid Cyber Responses Enabled by the Structure
During operations against ISIS, Cyber Command leveraged NSA surveillance to disrupt the group’s online communications within hours, not days. This speed was only possible because decision-making and intelligence processing were unified under one leadership structure. Instead of routing intelligence up and down competing chains of command, teams could seamlessly move from identifying critical nodes to launching cyber strikes.
Without such integration, adversaries might have had days, or weeks, to adapt, reroute their operations, or counterattack. In the digital battlespace, that margin of time could have allowed ISIS operatives to relocate, rebuild propaganda platforms, or coordinate violent plots.
Similar unified operations helped accelerate ransomware takedowns and disrupted foreign disinformation campaigns targeting U.S. elections, according to public statements by Cyber Command leadership in 2022 and 2023. These examples reinforce how tightly integrated command structures deliver results where time and agility are mission-critical.
2025 Leadership Turmoil and Renewed Split Debate
The abrupt dismissal of key NSA officials earlier this year, as reported by Reuters, reignited calls for separating the two organizations. Politicians and defense insiders now question whether a single leader can fairly balance two massive institutions without conflicts of interest.
The leadership shake-up has sharpened concerns that the dual-hat structure may obscure accountability and blur critical policy decisions. Critics argue that in a fast-evolving cyber landscape, where both intelligence priorities and military objectives are constantly shifting, the U.S. risks operational blind spots if one individual cannot adequately juggle the expanding missions of both NSA and Cyber Command.
Yet defenders of the dual-hat model caution that separating the two agencies would almost certainly introduce dangerous bureaucratic friction. In an era where cyberattacks can escalate from reconnaissance to disruption in a matter of hours, any new layers of command or coordination could undermine the United States’ ability to act swiftly and decisively.
The Origins of the NSA Cyber Command Dual Hat Structure
The Creation of Cyber Command in 2009
USCYBERCOM was officially established in 2009 to centralize U.S. military cyber operations, recognizing the growing importance of digital warfare. In the years leading up to its formation, cyber activities were spread across multiple military branches and commands, with no single unified leadership overseeing global cyber threats.
This fragmented structure created dangerous gaps in operational readiness. Intelligence was often collected without a direct mechanism for immediate action. Simultaneously, military cyber operations sometimes lacked the most current intelligence to properly target adversaries or defend assets. Senior defense officials warned that without an integrated cyber command, the United States would fall behind adversaries increasingly adept at exploiting digital vulnerabilities across military and civilian sectors.
The creation of Cyber Command marked a turning point: cyber operations were elevated to a strategic domain of warfare, comparable to land, sea, air, and space.
General Keith Alexander’s Role in Shaping the Model
General Keith Alexander, who served as both NSA Director and the first Commander of Cyber Command, shaped the dual-hat arrangement. His rationale was simple but powerful: no military cyber operation should be launched without real-time intelligence, and no intelligence should be collected without considering its operational application.
Alexander believed that keeping the NSA and Cyber Command under one leader would eliminate stovepipes, streamline mission execution, and enable rapid, data-driven offensive and defensive cyber operations. His vision emphasized speed, unity, and strategic flexibility at a time when cyber capabilities were evolving faster than traditional military doctrines could adapt.
Early Benefits of the NSA Cyber Command Dual Hat Arrangement
The early years of the dual-hat model validated this strategic logic. Cyber campaigns against nation-state actors like Iran demonstrated how quickly the United States could coordinate surveillance and strikes under unified leadership. One prominent example is Operation Olympic Games, widely reported by major media outlets, where a sophisticated cyber weapon known as Stuxnet disrupted Iran’s nuclear program.
While Operation Olympic Games remains classified in many respects, experts agree that the operation’s success depended on seamless coordination between intelligence gathering, malware deployment, and real-time operational adaptation, all hallmarks of the dual-hat system.
These early successes established the dual-hat leadership model as not just a bureaucratic arrangement, but a proven operational advantage in the emerging battlespace of cyber warfare.
Key Arguments for a Split
Oversight, Transparency, and Accountability Concerns
Some policymakers argue that the NSA Cyber Command dual hat creates blurred accountability. PBS notes that critics believe separate leadership would improve oversight and ensure clearer lines of responsibility (PBS). In the current model, it can be difficult to determine where intelligence decisions end and military operational decisions begin, especially during complex cyber engagements that involve both surveillance and active disruption.
Advocates for a split emphasize that having a military officer focus solely on cyber warfare, while a civilian or intelligence leader manages surveillance, could, on paper, better align with democratic oversight standards. They argue that dual-hatting one individual over both agencies gives enormous operational power without sufficient external checks, potentially complicating congressional oversight responsibilities. Clearer separation of duties, proponents say, would allow intelligence operations to be evaluated independently from military actions, leading to improved transparency for both the public and policymakers.
Mission Divergence: Intelligence vs. Combat Operations
The missions of NSA and Cyber Command have diverged significantly over time. While the NSA’s core mission remains the clandestine gathering and analysis of foreign signals intelligence, Cyber Command’s mandate focuses on overt offensive operations and defending military networks from hostile intrusion.
Axios reports that conflicting priorities could worsen if a single leader must constantly navigate two fundamentally different mandates (How firing the NSA leader could lead to Cyber Command’s split – Axios). Intelligence agencies prioritize secrecy, patience, and maintaining long-term access to adversary networks. In contrast, military cyber operations often demand swift, aggressive action to neutralize threats. These competing imperatives create an inherent tension: striking too soon can burn valuable intelligence sources, while delaying military action could allow adversaries to exploit vulnerabilities.
Splitting leadership could theoretically allow each agency to pursue its mission with greater clarity and strategic consistency, avoiding internal conflicts over when, and how, to act.
Political and Organizational Pressures
Congress and Pentagon leadership have long pushed for a clearer separation, arguing that the growth of Cyber Command into a fully mature combatant command justifies its own independent leadership (DefenseScoop).
Since its elevation to a unified combatant command in 2018, Cyber Command has steadily gained operational authority and resources. Lawmakers contend that as Cyber Command continues to mature, its structure should align with traditional military command models, where civilian intelligence agencies and military commands are clearly distinct entities.
Additionally, political pressure has increased amid broader debates over the role of surveillance and the military in democratic societies. Critics argue that an organization wielding both intelligence-gathering and offensive power under one leader could create troubling perceptions, or realities, of unchecked authority in cyberspace.
These political and organizational dynamics suggest that the debate over splitting the NSA and Cyber Command is no longer a theoretical question of efficiency; it is becoming a strategic and constitutional issue about the balance of power and democratic control in the digital age.
5 Devastating Risks If the Split Happens
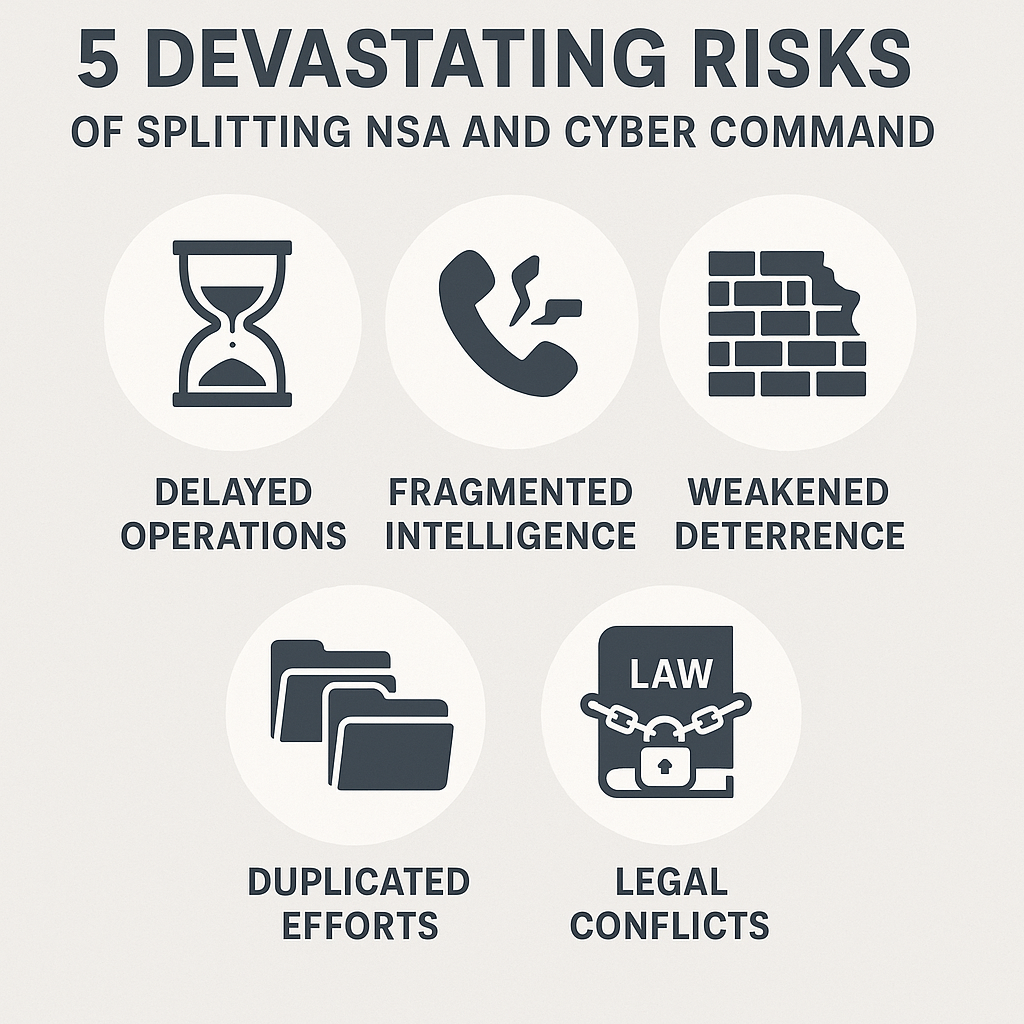
Delayed Offensive Cyber Operations
Splitting leadership could slow urgent responses to cyberattacks. DefenseScoop notes that having two separate chains of command would increase complexity and decision-making times during emergencies.
In cyber conflict, even minutes of hesitation can tip the balance. During the 2016 cyber operations against ISIS (Operation Glowing Symphony), U.S. forces had to move quickly to disrupt communications and propaganda before the group could shift to encrypted platforms. Military officials later credited rapid intelligence-to-action capabilities, fostered by the dual-hat structure, for the operation’s success. If separated, a similar campaign today might suffer critical delays while coordinating between two distinct leadership chains.
In a real-world cyber battle, delayed action often means losing the initiative entirely, an unacceptable risk when adversaries move at machine speed.

Fragmented Intelligence and Communication Breakdowns
FedScoop and Axios highlight fears that splitting NSA and Cyber Command would lead to fragmented intelligence pipelines, making it harder to rapidly convert raw data into actionable operations (FedScoop).
Without a tightly woven fabric of intelligence and operational decision-making, critical threats could slip through unnoticed. During the 2020 SolarWinds cyber espionage campaign, analysts later concluded that communication gaps between agencies contributed to the delayed discovery and response. Although not directly tied to a split leadership structure, the episode serves as a warning: even slight information silos can allow adversaries to operate undetected for months.
Splitting NSA and Cyber Command could institutionalize such vulnerabilities, leaving U.S. military, intelligence, and civilian systems more exposed to stealthy, long-term infiltration campaigns.
Weakened Deterrence Posture Against Adversaries
Military leaders like General Milley have warned that separation could weaken America’s cyber deterrence by signaling disorganization to adversaries (Defense One).
Countries like Russia and China may see a split as an invitation to become more aggressive in cyberspace. Deterrence relies not only on capability but also on the perception of readiness and unity. A bifurcated cyber structure could give adversaries the impression that U.S. responses will be slower, less cohesive, and easier to exploit.
The Volt Typhoon cyber campaign, attributed to Chinese state-sponsored hackers in 2024, showed how sophisticated actors now systematically target civilian and military networks simultaneously. Disorganization—or even the perception of it—could embolden adversaries to push further into critical infrastructure, knowing a divided U.S. response could slow countermeasures.
Operational Inefficiencies and Duplicative Bureaucracy
The Heritage Foundation warns that separating the agencies could lead to expensive duplication of technical and human resources (The Heritage Foundation).
Separate bureaucracies might create bottlenecks that slow operations even during crises. Each agency would require its own full spectrum of cyber defense and offense teams, its own legal support, operational planning staffs, and coordination mechanisms. Instead of streamlining operations, splitting could burden both agencies with redundant administrative overhead—driving up costs while reducing efficiency.
In the private sector, cybersecurity incidents often escalate when internal communications falter between IT security and executive leadership. In a national security context, duplicative command structures could produce similar breakdowns on a far more catastrophic scale.
Legal Conflicts Slowing Response Times
Differing authorities for intelligence (Title 50) and military (Title 10) operations could trigger legal disputes about who can act and when—a dangerous delay when an attack is already underway (The Heritage Foundation).
For example, if Cyber Command detects a cyberattack that crosses from military systems into civilian networks, determining which agency has jurisdiction could become a legal maze. Does it fall under domestic intelligence collection authority? Military defense of infrastructure? Emergency action under national security exceptions?
Even under the current dual-hat system, such questions are complex. A split would add additional legal firewalls, forcing commanders and analysts to navigate bureaucratic uncertainty in the middle of a live cyber incident. In cyberwarfare, hesitation caused by unclear legal mandates can be just as dangerous as technical failure.
Impact on U.S. Offensive Cyber Capabilities
Integration of Intelligence and Operations at Risk
Today’s seamless integration allows U.S. offensive cyber capabilities to hit faster, smarter, and harder. Splitting NSA and Cyber Command would risk losing that edge.
At present, intelligence collected by the NSA can be translated almost immediately into operational plans executed by Cyber Command. Analysts and operators sit side-by-side in secure environments, enabling real-time collaboration between those monitoring foreign adversaries and those preparing digital strikes. This fluid relationship ensures that threat actors can be tracked, assessed, and neutralized with minimal bureaucratic delay.
Splitting the agencies could fracture this bond, creating physical, operational, and cultural barriers between the “collectors” and the “fighters.” Intelligence would have to be vetted, packaged, and formally transferred through layers of command and legal review—costing precious time in an environment where milliseconds often make the difference between success and failure.
In a world where AI cyberattacks are exploding, unified operations are more important than ever. New AI-driven malware strains, autonomous reconnaissance bots, and machine-learning-optimized ransomware campaigns are already shortening attack windows. For a deeper breakdown of these emerging threats, explore our guide on AI Cyberattacks Are Exploding: Top AI Security Tools to Stop Deepfake Phishing & Reinforcement Learning Hacks in 2025.
Real-World Examples of Disrupted Cyber Campaigns
In previous operations against Iranian hackers, delays in coordination between surveillance and strike teams almost compromised missions, highlighting the dangers of disjointed efforts.
In one widely reported case, U.S. cyber forces detected a pending Iranian attack on U.S. naval assets. Rapid action was needed to disable command-and-control servers before the adversary could shift to alternate infrastructure. Had intelligence and operational leadership been separated at that moment, the lag in communication and approval processes could have allowed the Iranian team to launch their attack, causing significant operational disruption or even loss of life.
Strategic Advantage Loss Against Sophisticated Adversaries
Russia’s coordinated cyber operations against Ukraine show how adversaries capitalize on even small delays. In 2022, Russian cyber teams used combined cyber and kinetic attacks to disrupt communications infrastructure hours before missile strikes, demonstrating a brutally effective model of cyberwarfare synergy.
Losing the integrated capabilities between NSA and Cyber Command could embolden such actions against the U.S. Future adversaries like Russia, China, Iran, or North Korea may exploit even slight gaps in U.S. cyber readiness to pre-position malware inside critical infrastructure, manipulate information environments, or cripple military systems at the outset of a broader conflict.
In the evolving cyber battlespace, maintaining the fastest, most coordinated response capability is not merely advantageous—it is existential.
Potential for Major Intelligence Failures in 2025
Historical Lessons from the 9/11 Intelligence Failures
Brookings documents how poor coordination among agencies before 9/11 contributed to one of America’s greatest security failures (9/11 and the reinvention of the U.S. intelligence community – Brookings). In the years leading up to the attacks, intelligence about terrorist activity was scattered across agencies like the FBI, CIA, and NSA, but no single entity had both the visibility and the authority to piece the information together and act decisively.
The catastrophic outcome reinforced a hard truth: divided intelligence structures create blind spots. Splitting NSA and Cyber Command could risk repeating those mistakes at a time when threats are increasingly digital, faster-moving, and harder to detect. In the cyber domain, even a few missed signals could mean the difference between repelling an attack and suffering a major breach of critical infrastructure, financial systems, or national security assets.
Unified command under NSA and Cyber Command has helped ensure that signals intelligence (SIGINT) feeds directly into operational cyber defense. Fragmenting this structure now would increase the risk of information silos, delayed responses, and critical threat vectors going unnoticed—recreating the dangerous conditions that led to past intelligence failures.
The Complexity of Modern Cyber Threats
Today’s cyber threats are vastly more complex than even a decade ago. Ransomware attacks, AI voice cloning scams, deepfake phishing, and sophisticated nation-state cyber espionage campaigns all require speed, unity, and precision in detection and response.
Disorganization could be fatal. Attackers now use machine learning and autonomous systems to identify and exploit vulnerabilities within hours—or even minutes—of discovering them. Without the tight coordination that NSA and Cyber Command currently provide, the U.S. could face longer reaction times, conflicting priorities, and gaps in defensive coverage.
Our recent report on Shocking Rise in AI Voice-Cloning Scams: 5 Cybersecurity Threats You Must Know highlights how adversaries are already using AI to scale social engineering attacks in ways traditional defense systems struggle to counter. These emerging threats demand a tightly unified approach to cyber defense—one that fragmentation between NSA and Cyber Command would severely undermine.
Increased Breach Risks Across Civilian and Military Networks
Fragmented cyber defenses would leave military, infrastructure, and civilian systems increasingly vulnerable to undetected breaches. Adversaries such as China’s Volt Typhoon group have already demonstrated the ability to infiltrate civilian communications and energy infrastructure while avoiding traditional defense perimeters.
Without seamless information sharing and operational synchronization between NSA and Cyber Command, attackers could move laterally across networked systems without immediate detection. This risk is particularly acute for hybrid threats that blur the line between civilian and military targets—one of the defining characteristics of modern cyber conflict.
As threats grow more interconnected, splitting NSA and Cyber Command could leave gaping holes in America’s cyber shield, creating opportunities that sophisticated adversaries are fully prepared to exploit.

Lessons from Past Agency Breakups
The Disbanding of the Office of Strategic Services (OSS)
After World War II, dismantling the Office of Strategic Services (OSS) created an intelligence vacuum that left the U.S. blind to emerging threats for years (Intelligence Failures – Hoover Institution). The OSS had been instrumental in coordinating intelligence across theaters of war, but its sudden disbanding in 1945 fragmented U.S. intelligence efforts just as the geopolitical landscape was shifting toward Cold War tensions.
In the vacuum that followed, U.S. agencies struggled to adapt to emerging Soviet threats, leading to disjointed efforts that hindered early strategic positioning. It took years—and significant national security setbacks—before the intelligence community was restructured into a more effective system.
The cautionary tale here is clear: dismantling a proven intelligence framework can create unforeseen vulnerabilities that adversaries are quick to exploit. Splitting NSA and Cyber Command risks repeating this cycle, just as cyber threats reach unprecedented levels of complexity and speed.
Department of Homeland Security Integration Struggles
The creation of the Department of Homeland Security (DHS) after the 9/11 attacks provides a more recent lesson. DHS was formed by merging 22 separate federal departments and agencies under one umbrella. While the goal was better coordination, the early years of DHS were marked by severe integration struggles, cultural clashes between agencies, and a lack of clear operational leadership.
Many analysts argue these issues contributed to missed warning signs during Hurricane Katrina and other crises in the mid-2000s. Instead of enhancing security immediately, the initial integration weakened response capabilities at critical moments.
Lessons here reinforce why tightly integrating cyber functions matters more than ever. The operational cohesion achieved by combining NSA and Cyber Command leadership could be lost if bureaucratic barriers are reintroduced, just as the volume and sophistication of cyber threats are increasing exponentially.
Just as insider risks have risen sharply in the last decade, disorganization could allow internal threats to grow unchecked. We explore these dangers further in Encrypted Messaging Crisis: 5 Critical Lessons from Signalgate, where emerging technologies are enabling insider breaches at alarming new scales.
Relevance to Modern Cyber-Intelligence Structures
Modern cyber conflicts demand the kind of unity that past agency failures lacked. Threat actors today move faster, operate across civilian and military sectors simultaneously, and use AI to scale attacks.
Splitting NSA and Cyber Command risks losing the unified intelligence and operational synchronization that modern cybersecurity—and modern national security—absolutely require. Fragmentation would not merely recreate historical problems; it could amplify them in a threat environment where milliseconds, not months, determine the outcome of major national security events.
In short, history shows that when coordination fails, security fails. And in the cyber domain, the margin for error is now razor-thin.
Conclusion: A Dangerous Gamble for U.S. Cybersecurity
Splitting NSA and Cyber Command might seem like a bureaucratic upgrade—but it’s a gamble with America’s cyber defenses. The risks are not theoretical. Coordination delays, fragmented intelligence, weakened deterrence, and operational bottlenecks could put the nation at serious risk at a time when cyber warfare is accelerating rapidly.
The dual-hat leadership model between NSA and Cyber Command was not created by accident. It emerged from the painful lessons of past intelligence failures and the recognition that speed, unity, and seamless operational coordination are essential for modern national security. Severing this relationship could recreate the very vulnerabilities that America has worked for two decades to overcome.
As AI accelerates cyber threats and adversaries become more aggressive, maintaining a tightly unified cyber command structure is no longer a luxury—it is a strategic necessity. Emerging technologies like AI-driven malware, autonomous reconnaissance systems, and advanced social engineering attacks are shortening the timeline between network compromise and catastrophic disruption. In this environment, any delays caused by divided leadership between NSA and Cyber Command could be exploited ruthlessly by adversaries like China, Russia, Iran, or non-state actors.
Policymakers must weigh the real-world operational costs of a split—not just political appearances or abstract notions of organizational purity. The stakes are measured not in theoretical risks but in real vulnerabilities across critical infrastructure, military readiness, and civilian life.
The lessons of history are stark: when coordination fails, national security fails. If NSA and Cyber Command are separated without extraordinary safeguards—and even then—the United States risks facing the next major cyber crisis divided, delayed, and dangerously exposed.
We cover unfolding cybersecurity stories like this in our newsletter—subscribe here to stay ahead of emerging threats and strategic shifts shaping the future of cyber conflict.
Key Takeaways
- Splitting NSA and Cyber Command could drastically slow cyber responses.
- Fragmented intelligence pipelines would weaken national security.
- Past intelligence failures show the dangers of disjointed structures.
- Operational inefficiencies could severely impact U.S. offensive capabilities.
- Maintaining dual-hat leadership preserves vital speed and cohesion.
FAQ Section
Q1: What is the NSA Cyber Command dual-hat arrangement?
A1: One person leads both the NSA and Cyber Command to streamline intelligence and cyber operations.
Q2: Why are some pushing for a Cyber Command split?
A2: Concerns include oversight, mission conflict, and clarity of command.
Q3: What risks come with splitting them?
A3: Delayed responses, fragmented intelligence, weakened deterrence, and legal confusion.
Q4: Has history shown the dangers of splitting agencies?
A4: Yes—post-OSS disbandment and early DHS struggles highlight the risks.
Q5: Can oversight be improved without a split?
A5: Experts argue it can—through governance reforms without dismantling operational unity.
